Certified Ethical Hacker (CEH) v12 Training



Certified Ethical Hacker (CEH) v12 Training
Certified Ethical Hacker (CEH) v12 E-Learning Training Certified Teachers Exam Quizzes Online Mentor MeasureUp Test Exam Live Labs Tips Tricks Certificate.
Read more- Brand:
- EC-Council
- Discounts:
-
- Buy 2 for €293,02 each and save 2%
- Buy 3 for €290,03 each and save 3%
- Buy 4 for €287,04 each and save 4%
- Buy 5 for €284,05 each and save 5%
- Buy 10 for €269,10 each and save 10%
- Buy 25 for €254,15 each and save 15%
- Buy 50 for €239,20 each and save 20%
- Availability:
- In stock
- Delivery time:
- Ordered before 5 p.m.! Start today.
- Award Winning E-learning
- Lowest price guarantee
- Personalized service by our expert team
- Pay safely online or by invoice
- Order and start within 24 hours
Certified Ethical Hacker (CEH) v12 Training - OEM Certkit
The Certified Ethical Hacker has been battle-hardened over the last 20 years, creating hundreds of thousands of Certified Ethical Hackers employed by top companies, militaries, and governments worldwide.
The CEH v12 also equips aspiring cybersecurity professionals with the tactics, techniques, and procedures (TTPs) to build ethical hackers who can uncover weaknesses in nearly any type of target system before cybercriminals do.
Who should attend:
The Certified Ethical Hacking training course will significantly benefit security officers, Cybersecurity auditors, security professionals, Site administrators, Security Analyst and anyone who is concerned about the integrity of the network infrastructure.
CertKit content:
•E-learning courses:
CEH v12: Cybersecurity Concepts, Attacks, and Information Warfare
Course: 1 Hour, 35 Minutes
- CEH v12 EC-Council Certification Overview
- Basic Cybersecurity Concepts
- Attacker Motives, Goals, and Objectives
- Attack Classifications
- Information Warfare
CEH v12: Cyber Kill Chain, TTPs, Behaviors, and Threat Hunting
Course: 1 Hour, 17 Minutes
- Cyber Kill Chain
- Tactics, Techniques, and Procedures
- Common Adversarial Behaviors
- Threat Hunting Concepts
CEH v12: Risk Management, Cyber Threat Intelligence, and Threat Modeling
Course: 54 Minutes
- Risk and Risk Management
- Cyber Threat Intelligence
- Threat Modeling
CEH v12: Incident Management, ML, AI, and Regulations
Course: 1 Hour, 10 Minutes
- Incident Management Handling and Response
- Machine Learning (ML) and Artificial Intelligence (AI)
- Standards and Regulations
CEH v12: Hacking Methodology, MITRE ATT&CK Framework, and Diamond Model
Course: 1 Hour, 5 Minutes
- CEH Hacking Methodology
- MITRE ATT&CK Framework1
- Diamond Model of Intrusion Analysis
CEH v12: Footprinting, Google Dorks, Search Engines, and Subdomains
Course: 1 Hour, 22 Minutes
- Footprinting Concepts
- Google Dorks
- Shodan Censys and Thingful
- Subdomain Enumeration
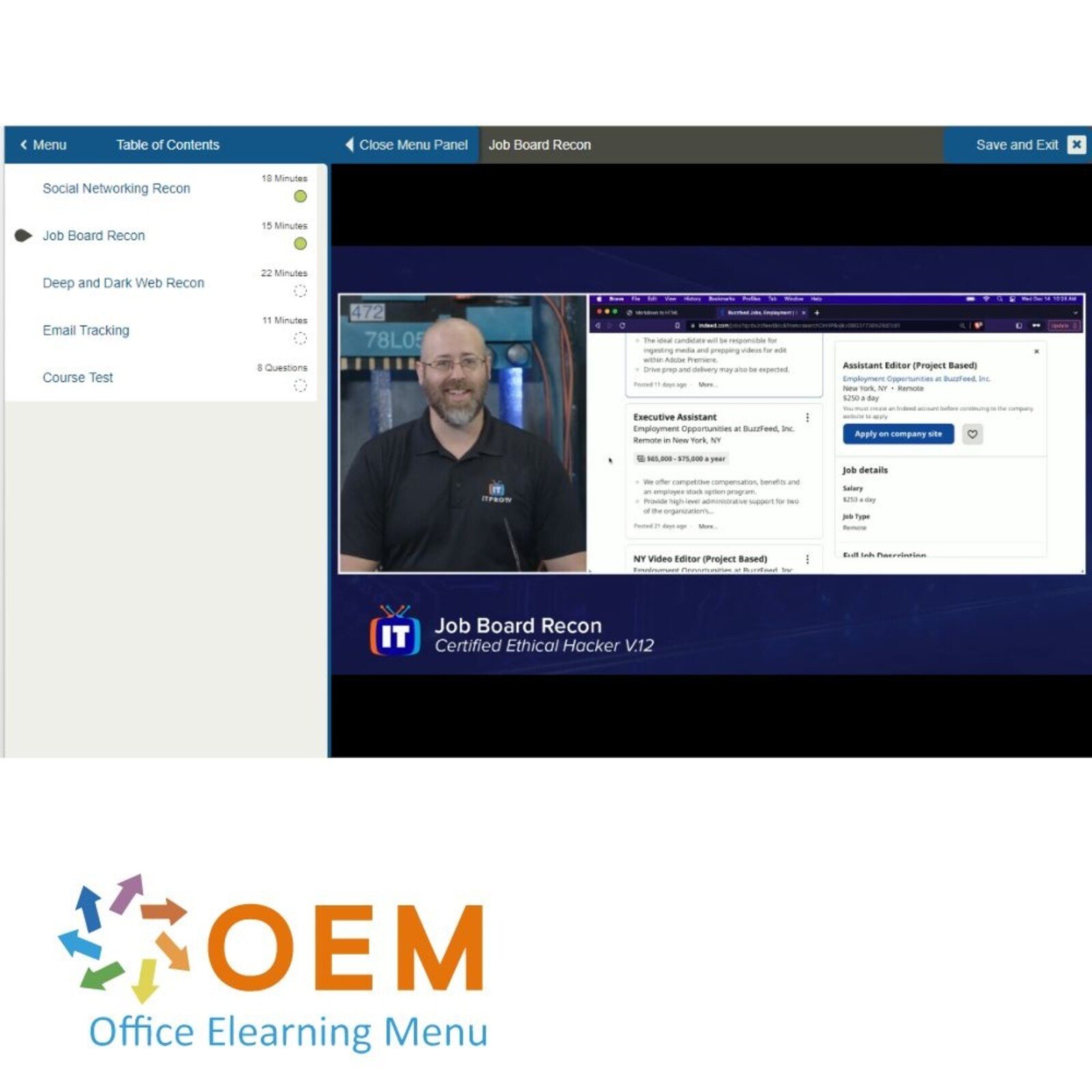
CEH v12: Recon Tools and Tactics
Course: 1 Hour, 7 Minutes
- Social Networking Recon
- Job Board Recon
- Deep and Dark Web Recon
- Email Tracking
CEH v12: Footprinting and Social Engineering Recon and Countermeasures
Course: 1 Hour, 14 Minutes
- WHOIS and DNS Recon
- Social Engineering Recon
- Other Footprinting Tools
- Footprinting and Recon Countermeasures
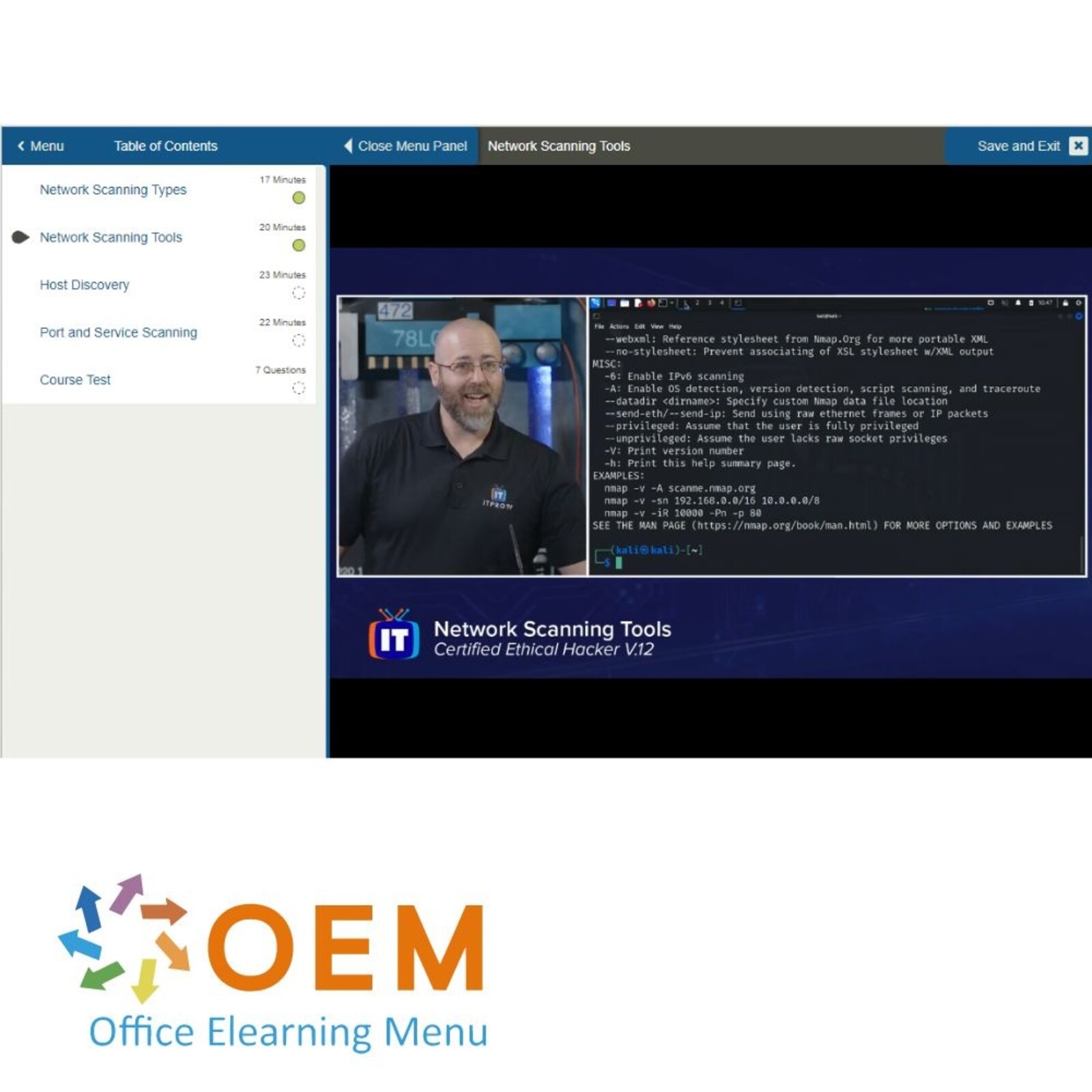
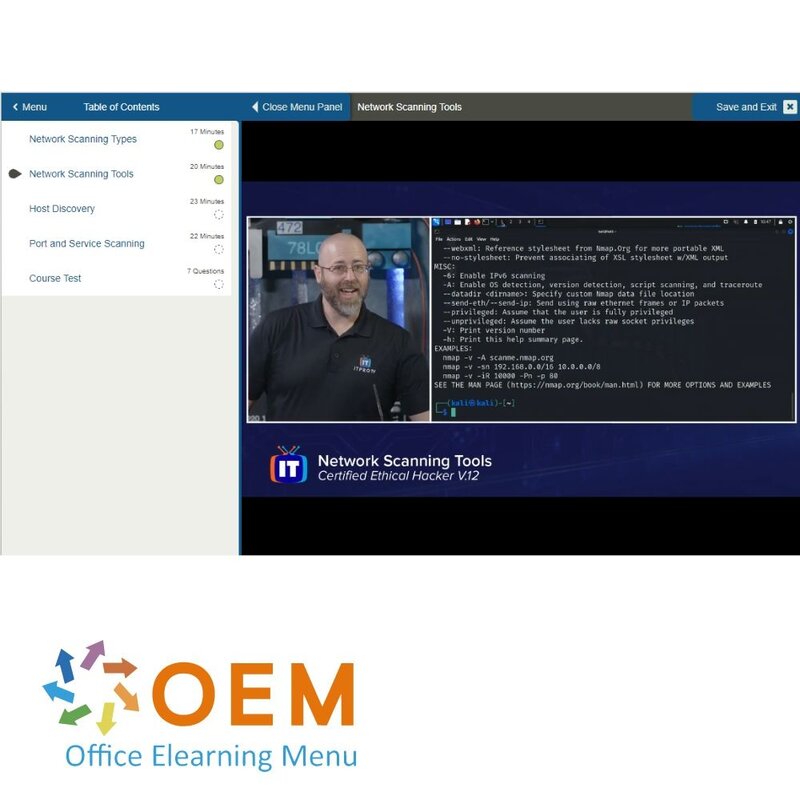
CEH v12: Network Scanning, TCP, Host Discovery, and Port/Service Scanning
Course: 1 Hour, 21 Minutes
- Network Scanning Types
- Network Scanning Tools
- Host Discovery
- Port and Service Scanning
CEH v12: Nmap TCP Scans
Course: 1 Hour, 23 Minutes
- TCP Connect Scan
- Stealth Scan
- Inverse TCP XMAS and Maimon Scans
- ACK Scan
CEH v12: Nmap IDLE IPID, UDP, and SCTP Scans
Course: 50 Minutes
- Nmap IDLE IPID Scan
- Nmap UDP Scan
- Nmap SCTP INIT Scan
CEH v12: Scan Optimization, OS Identification, and IDS/Firewall Evasion
Course: 55 Minutes
- Nmap Scan Optimizations
- Target OS Identification Techniques
- Intrusion Detection System (IDS) and Firewall Evasion
CEH v12: NetBIOS, SMB, SNMP, and LDAP Enumeration
Course: 1 Hour
- NetBIOS and Server Message Block (SMB) Enumeration
- Simple Network Management Protocol (SNMP) Enumeration
- Lightweight Directory Access Protocol (LDAP) Enumeration
CEH v12: NTP, NFS, SMTP, and FTP Enumeration
Course: 55 Minutes
- Network Time Protocol (NTP) Enumeration
- Network File System (NFS) Enumeration
- SMTP and FTP Enumeration
CEH v12: Passwords Attacks, Extraction, and Cracking
Course: 1 Hour
- Password Attack Concepts
- Password Extraction and Cracking
- Password Attacks Cracking Enhancement Techniques
CEH v12: Buffer Overflows, Privilege Escalation, and System Access
Course: 1 Hour, 30 Minutes
- Buffer Overflows
- Privilege Escalation
- Maintaining System Access
CEH v12: Steganography and Avoiding Detection
Course: 47 Minutes
- Steganography Tools and Techniques
- Covering Your Tracks
CEH v12: AD Enumeration, Mimikatz, and Pivoting Techniques
Course: 1 Hour, 15 Minutes
- AD Enumeration
- Mimikatz
- Pivoting
CEH v12: Malware, Threats, Trojans, and Viruses
Course: 1 Hour, 23 Minutes
- Malware Concepts and Components
- Advanced Persistent Threat (APT)
- Trojans
- Viruses and Worms
CEH v12: Fileless Malware, Malware Analysis, and Countermeasures
Course: 1 Hour, 11 Minutes
- Fileless Malware
- Malware Analysis
- Malware Countermeasures
CEH v12: Sniffing and Poisoning
Course: 1 Hour, 25 Minutes
- Network Sniffing Basics
- DHCP Sniffing Attacks
- ARP Poisoning
- DNS Poisoning
- Sniffing Defenses
CEH v12: Social Engineering, Insider Threats, and Identity Theft
Course: 1 Hour, 11 Minutes
- Social Engineering Concepts and Attacks
- Insider Threats
- Identity Theft
CEH v12: DoS, DDoS, Volumetric, and Protocol Attacks
Course: 58 Minutes
- DoS and DDoS Attacks
- Volumetric Attacks
- Protocol Attacks
CEH v12: App Layer Attacks, Botnets, and DoS Countermeasures
Course: 58 Minutes
- Application Layer Attacks
- Bots and Botnets
- DoS and DDoS Countermeasures
CEH v12: Hijacking Concepts and Countermeasures
Course: 1 Hour, 23 Minutes
- Session Hijacking Concepts
- Network Level Session Hijacking
- Application Level Session Hijacking
- Session Hijacking Countermeasures
CEH v12: Intrusion Detection and Prevention, Firewalls, and Honeypots
Course: 1 Hour, 11 Minutes
- IDS and IPS
- Firewalls
- Honeypots
CEH v12: Web App Hacking Methodology, CSRF Attacks, and Input Filter Evasion
Course: 1 Hour, 8 Minutes
- Web App Hacking Methodology
- Cross-Site Request Forgery (CSRF) Attacks
- Input Filtering Evasion
CEH v12: Web Application Attacks and Vulnerabilities
Course: 1 Hour, 9 Minutes
- Web App Concepts
- OWASP Top 10 Web Application Attacks
- Unvalidated Redirects and Forwards
CEH v12: Web App Hacking Methodology, CSRF Attacks, and Input Filter Evasion
Course: 1 Hour, 8 Minutes
- Web App Hacking Methodology
- Cross-Site Request Forgery (CSRF) Attacks
- Input Filtering Evasion
CEH v12: IDOR Attacks, File Inclusion Attacks, Web APIs, and Webhooks
Course: 52 Minutes
- Insecure Direct Object Reference (IDOR) Attacks
- Local File and Remote File Inclusion Attacks
- APIs and Webhooks
CEH v12: SQL Injection Concepts and Attacks
Course: 1 Hour, 10 Minutes
- SQL Injection Concepts
- Error-based SQLi Attacks
- Blind-based SQLi Attacks
CEH v12: SQL Injection and SQLMap
Course: 47 Minutes
- System Access with SQL Injection (SQLi)
- SQL Injection Testing with SQLMap
CEH v12: Wireless Concepts, Threats, and Hacking Tools
Course: 1 Hour, 7 Minutes
- Wireless Concepts
- Wireless Technology Threats
- Wireless Hacking Tools
CEH v12: Wireless Hacking and Countermeasures
Course: 49 Minutes
- Wireless Hacking
- Wireless Hacking Countermeasures
CEH v12: Mobile Hacking, OS Security, and Device Management
Course: 1 Hour, 30 Minutes
- Mobile Security Basics
- Android Security
- iOS Security
- Mobile Device Management
CEH v12: IoT Threats, Vulnerabilities, Attack Tools, and Countermeasures
Course: 1 Hour, 1 Minute
- Internet of Things (IoT) Concepts
- IoT Threats and Vulnerabilities
- IoT Attacks Tools and Countermeasures
CEH v12: Operational Technology Concepts, Attack Tools, and Countermeasures
Course: 53 Minutes
- Operational Technology (OT) System Concepts
- OT Attacks Tools and Countermeasures
CEH v12: Cloud Computing, Containers, Hacking, and Security Controls
Course: 1 Hour, 29 Minutes
- Cloud Computing Concepts
- Container Concepts
- Hacking Cloud Services
- Cloud Security Controls
CEH v12: Cryptography, Algorithms, Implementations, and Tools
Course: 1 Hour, 7 Minutes
- Cryptography Concepts
- Crypto Algorithms and Implementations
- Cryptography Tools
CEH v12: PKI, Cryptanalysis, and Attack Countermeasures
Course: 52 Minutes
- Public Key Infrastructure
- Cryptanalysis Methods
- Crypto-attack Countermeasures
Online Mentor
The online mentor can answer all your specific technical questions via chat or email related to your studies.
Online Mentor is active for 90 days or 365 days - after activation!
Tips, Tricks & Links
Take advantage of our comprehensive collection of tips, tricks and links designed specifically to support your preparation for certification exams. These resources offer valuable insights and proven strategies to make your studies more effective. Enhance your learning experience and approach your exams with confidence!
MeasureUp Exam simulation
- 200+ questions
Practice Labs - Virtual Labs (option)
Welcome to the Certified Ethical Hacker Practice Lab. The Certified Ethical Hacker certification is an intermediate penetration testing qualification that focuses on penetration testing techniques, identifying attack surfaces and identifying infrastructure vulnerabilities. The Certified Ethical Hacker Practice Lab’s primary focus is the practical application of the exam objectives, and theory objectives will not be covered. After completing this lab, you will have gained further knowledge on penetration testing techniques, identifying infrastructure vulnerabilities, and exploring the use of different network and application attack tools.
| Language | English |
|---|---|
| Qualifications of the Instructor | Certified |
| Course Format and Length | Teaching videos with subtitles, interactive elements and assignments and tests |
| MeasureUp Examination simulation | Included |
| Online Virtuele labs | Receive 12 months of access to virtual labs corresponding to traditional course configuration. Active for 365 days after activation, availability varies by Training |
| Tips & Tricks | Included |
| Exam Quiz | Included |
| Full training for the official Exam | Yes |
| Lesson duration | 47:07 Hours |
| Progress monitoring | Yes |
| Access to Material | 365 days |
| Technical Requirements | Computer or mobile device, Stable internet connections Web browsersuch as Chrome, Firefox, Safari or Edge. |
| Support or Assistance | Helpdesk and online knowledge base 24/7 |
| Certification | Certificate of participation in PDF format |
| Price and costs | Course price at no extra cost |
| Cancellation policy and money-back guarantee | We assess this on a case-by-case basis |
| Award Winning E-learning | Yes |
| Tip! | Provide a quiet learning environment, time and motivation, audio equipment such as headphones or speakers for audio, account information such as login details to access the e-learning platform. |
There are no reviews written yet about this product.
OEM Office Elearning Menu Top 2 in ICT-trainingen 2024!
OEM Office Elearning Menu is trots op de tweede plaats in de categorie ICT-trainingen 2024 bij Beste Opleider van Nederland (Springest/Archipel). Dank aan al onze cursisten voor hun vertrouwen!
Reviews
There are no reviews written yet about this product.