Cryptography Fundamentals Training

Cryptography Fundamentals Training
Cryptography Fundamentals Training Award-winning E-Learning course Extensive interactive videos with spoken text Certified teachers Practical exercises Certificate.
Read more- Discounts:
-
- Buy 2 for €146,02 each and save 2%
- Buy 3 for €144,53 each and save 3%
- Buy 5 for €138,57 each and save 7%
- Buy 10 for €134,10 each and save 10%
- Buy 25 for €126,65 each and save 15%
- Buy 50 for €116,22 each and save 22%
- Buy 100 for €104,30 each and save 30%
- Buy 200 for €74,50 each and save 50%
- Availability:
- In stock
- Delivery time:
- Ordered before 5 p.m.! Start today.
- Award Winning E-learning
- Lowest price guarantee
- Personalized service by our expert team
- Pay safely online or by invoice
- Order and start within 24 hours
Cryptography Fundamentals E-Learning
Order this amazing, award-winning Cryptography Fundamentals E-Learning Training today!
✔️ 1 year 24/7 access to extensive interactive videos, speeches and practical tasks.
✔️ Track your progress with reports and tests.
✔️ Receive a certificate of participation upon successful completion of the course.
Why choose this course?
In a world where digital communications and data security are crucial, cryptography has become an essential tool for IT professionals. This course provides a solid foundation in cryptography and helps you understand the principles and applications of this technology.
What makes this course unique:
- Extensive interactive content: Learn through videos, examples and hands-on exercises.
- Award-winning learning method: Recognized for the quality of content and approach.
- Practical skills: Apply cryptographic techniques in real-world scenarios.
- Progress monitoring: Track your performance with reports and tests per chapter.
Who should participate?
This course is designed for:
- IT professionals looking to expand their knowledge of data security.
- Security specialists who want to develop expertise in cryptography.
- Students considering a career in cybersecurity.
- Software developers who want to design and build secure applications.
- Anyone interested in the fundamentals of encryption and data security.
Course content
Cryptography Fundamentals: Defining Cryptography
What is Cryptography
Course: 28 Minutes
- Course Introduction
- Introducing Cryptography
- Identifying Historical Use of Cryptography
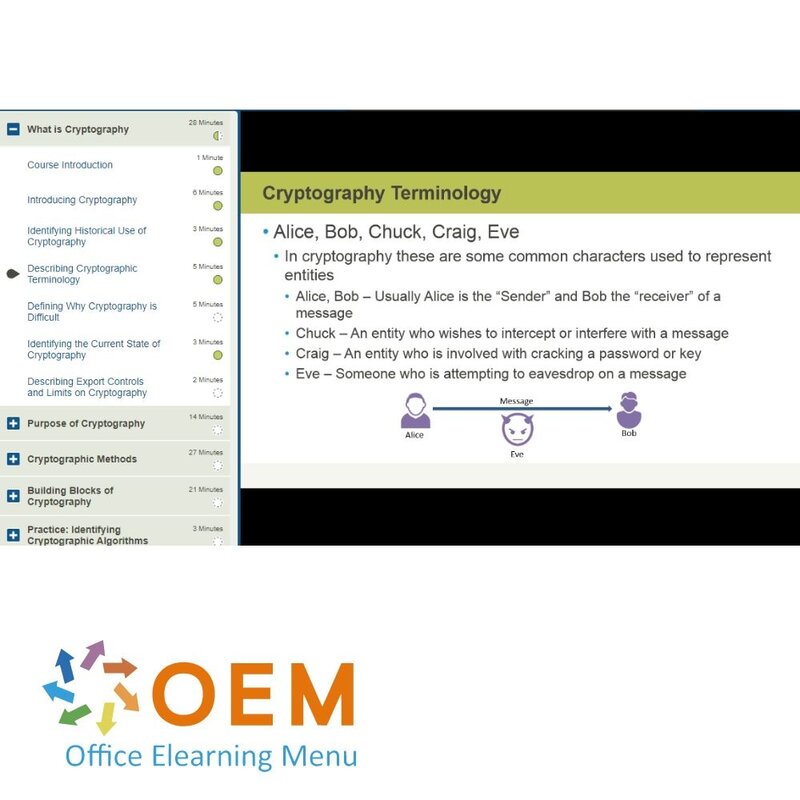
- Describing Cryptographic Terminology
- Defining Why Cryptography is Difficult
- Identifying the Current State of Cryptography
- Describing Export Controls and Limits on Cryptography
Purpose of Cryptography
Course: 14 Minutes
- Describing How Cryptography Provides Confidentiality
- Recognizing the Need for Data Integrity
- Defining Cryptography Authentication
- Applying Non-repudiation to Cryptography
Cryptographic Methods
Course: 27 Minutes
- Using a One-time Pad
- Describing Substitution Ciphers
- Using Symmetric Algorithms
- Working with Asymmetric Algorithms
- Hiding Data Using Steganography
- Using One-way Hashes
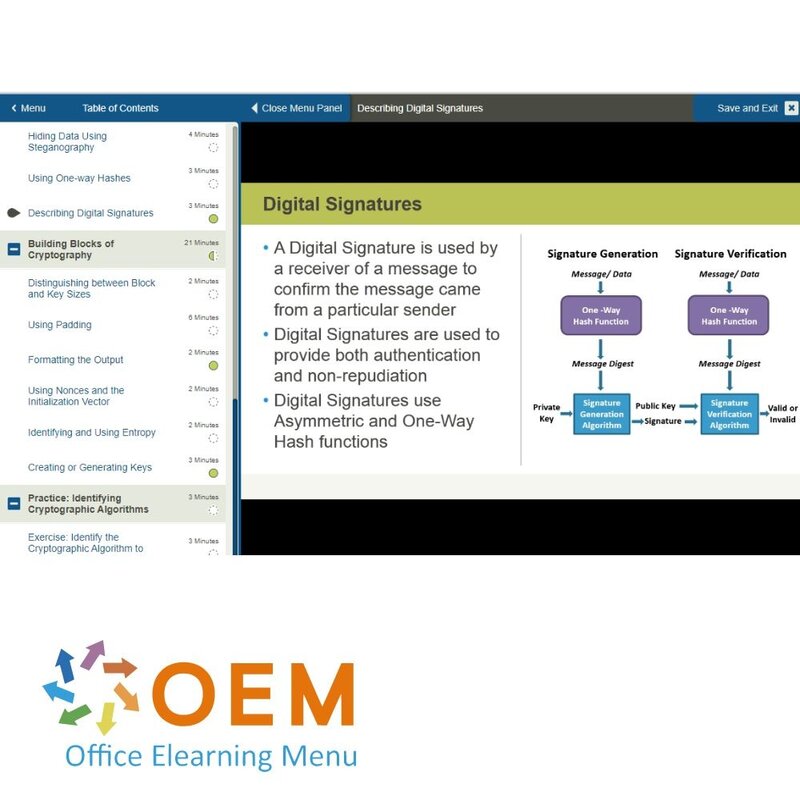
- Describing Digital Signatures
Building Blocks of Cryptography
Course: 21 Minutes
- Distinguishing between Block and Key Sizes
- Using Padding
- Formatting the Output
- Using Nonces and the Initialization Vector
- Identifying and Using Entropy
- Creating or Generating Keys
Practice: Identifying Cryptographic Algorithms
Course: 3 Minutes
- Exercise: Identify the Cryptographic Algorithm to Use
Modes of Operation
Course: 24 Minutes
- Course Introduction
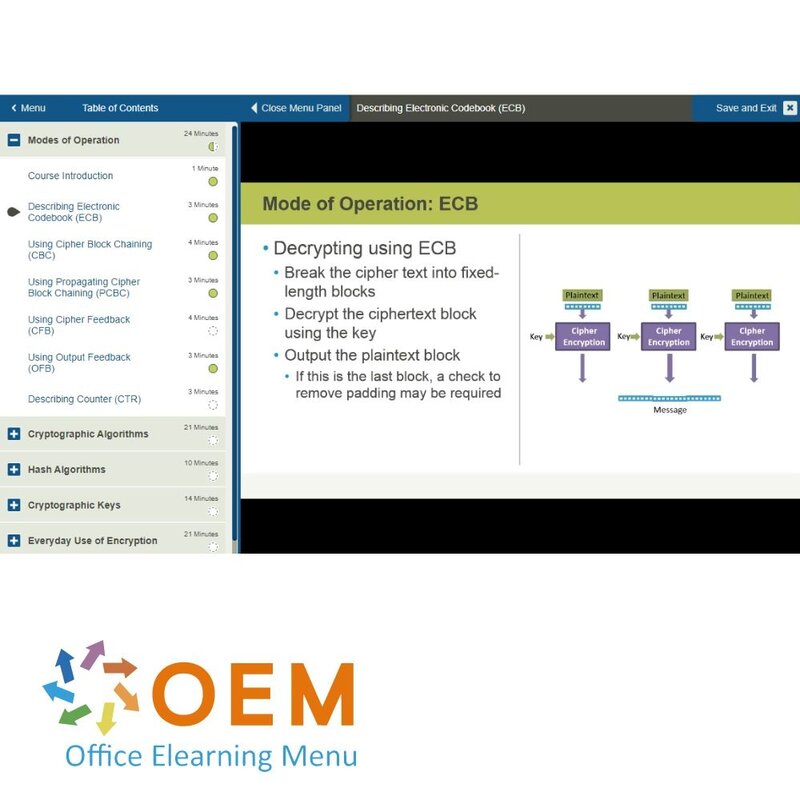
- Describing Electronic Codebook (ECB)
- Using Cipher Block Chaining (CBC)
- Using Propagating Cipher Block Chaining (PCBC)
- Using Cipher Feedback (CFB)
- Using Output Feedback (OFB)
- Describing Counter (CTR)
Cryptographic Algorithms
Course: 21 Minutes
- Using the AES Block Algorithm
- Applying the DES/3DES Block Algorithm
- Describing the Blowfish Block Algorithm
- Describing the RC4 Streaming Algorithm
- Describing the ElGamal Algorithm
- Defining the RSA Algorithm
Hash Algorithms
Course: 10 Minutes
- Describing MD5, SHA1, and SHA
- Using SHA
- Describing HMAC
Cryptographic Keys
Course: 14 Minutes
- Describing Key Management
- Describing Key Exchange
- Describing Key Escrow
Everyday Use of Encryption
Course: 21 Minutes
- Identifying Secure Communications Over HTTPS
- Working with the Secure Shell (SSH)
- Using GPG with E-mail
- Working with Disk Encryption
Analysis
Course: 12 Minutes
- Identifying Algorithm and Key Strengths
- Describing Cryptanalysis
- Describing Side-channel Attacks
Practice: Applying Modes and Key Management
Course: 4 Minutes
- Exercise: Apply Cryptographic Modes and Algorithms
Get started today!
✔️ Instant access to all course materials so you can start right away.
✔️ Interactive exercises to master cryptographic concepts.
✔️ Certificate of participation to validate your knowledge and skills.
Order your course now and develop your expertise in cryptography!
| Language | English |
|---|---|
| Qualifications of the Instructor | Certified |
| Course Format and Length | Teaching videos with subtitles, interactive elements and assignments and tests |
| Lesson duration | 3:27 Hours |
| Progress monitoring | Yes |
| Access to Material | 365 days |
| Technical Requirements | Computer or mobile device, Stable internet connections Web browsersuch as Chrome, Firefox, Safari or Edge. |
| Support or Assistance | Helpdesk and online knowledge base 24/7 |
| Certification | Certificate of participation in PDF format |
| Price and costs | Course price at no extra cost |
| Cancellation policy and money-back guarantee | We assess this on a case-by-case basis |
| Award Winning E-learning | Yes |
| Tip! | Provide a quiet learning environment, time and motivation, audio equipment such as headphones or speakers for audio, account information such as login details to access the e-learning platform. |
There are no reviews written yet about this product.
OEM Office Elearning Menu Top 2 in ICT-trainingen 2024!
OEM Office Elearning Menu is trots op de tweede plaats in de categorie ICT-trainingen 2024 bij Beste Opleider van Nederland (Springest/Archipel). Dank aan al onze cursisten voor hun vertrouwen!
Reviews
There are no reviews written yet about this product.