Getting Started with Information Security Training

Getting Started with Information Security Training
Order this unique E-Learning Training Getting Started with Information Security online, 1 year 24/7 access to rich interactive videos, progress through reporting and testing.
Read more- Discounts:
-
- Buy 2 for €155,82 each and save 2%
- Buy 3 for €154,23 each and save 3%
- Buy 4 for €152,64 each and save 4%
- Buy 5 for €151,05 each and save 5%
- Buy 10 for €143,10 each and save 10%
- Buy 25 for €135,15 each and save 15%
- Buy 50 for €127,20 each and save 20%
- Availability:
- In stock
- Delivery time:
- Ordered before 5 p.m.! Start today.
- Award Winning E-learning
- Lowest price guarantee
- Personalized service by our expert team
- Pay safely online or by invoice
- Order and start within 24 hours
Getting Started with Information Security E-Learning
Order this unique E-Learning course today!
✔️ 1 year 24/7 access to interactive videos, voice and progress monitoring through reports.
✔️ Direct tests per chapter to immediately test and strengthen your knowledge.
Why choose this course?
In today's digital world, information security is essential for organizations and individuals to protect data from threats such as cyber attacks and data breaches. This course provides a comprehensive introduction to information security, helping you learn the fundamentals of the field and understand why it is so important.
What you will learn:
- The Basics of Information Security: Learn the core concepts and principles that form the backbone of effective security.
- Risk analysis and management: Understand how to identify, assess and manage risks to keep data safe.
- Cyber threats and countermeasures: Understand the types of cyber threats and how to combat them.
- Security Policies and Procedures: Learn how to create and implement effective security policies.
- Compliance and regulations: Discover how information security relates to laws and regulations, such as GDPR and ISO 27001.
Who should participate?
This course is suitable for:
- IT professionals who want to expand their knowledge of information security.
- Business leaders and managers who want to understand and manage the risks of cyber threats.
- Beginners in IT security who want to build a solid foundation in the field.
- Students and job seekers who want to start a career in cybersecurity.
- Anyone interested in learning information security concepts.
Course content
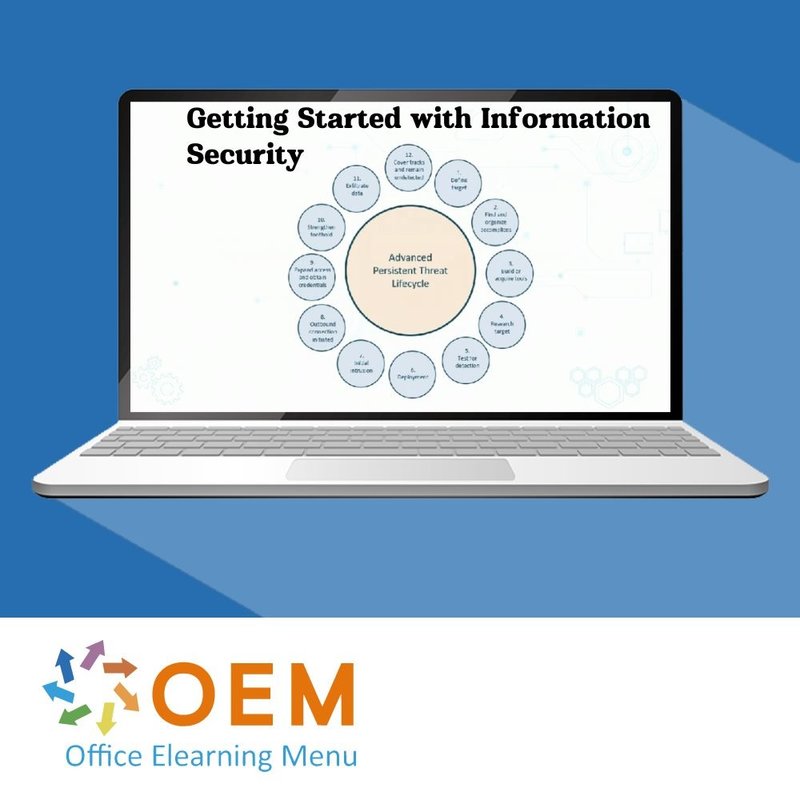
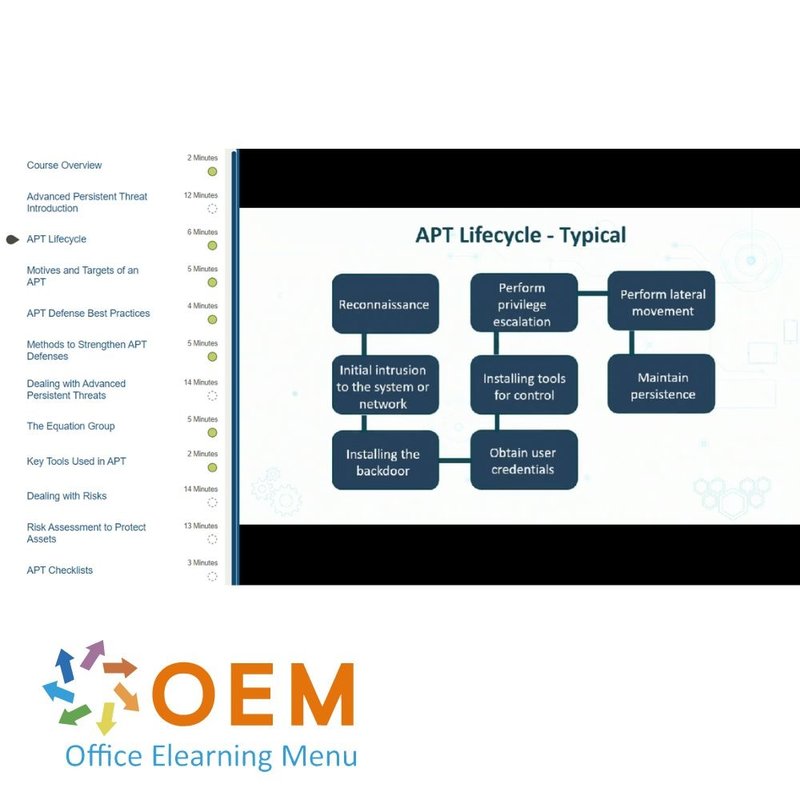
Information Security: APT Defenses
Course: 1 Hour, 26 Minutes
- Course Overview
- Advanced Persistent Threat Introduction
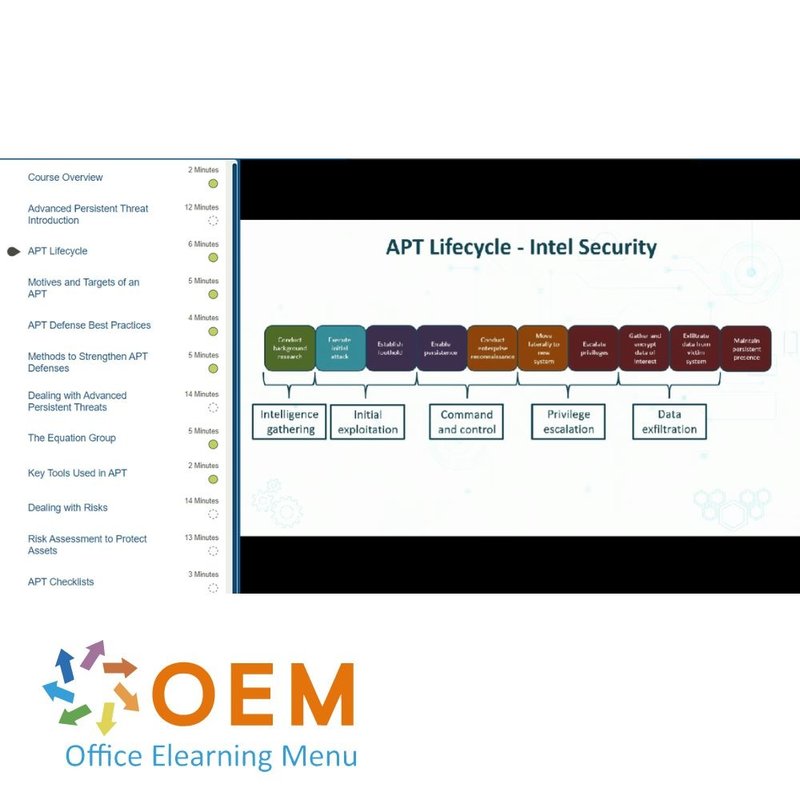
- APT Lifecycle
- Motives and Targets of an APT
- APT Defense Best Practices
- Methods to Strengthen APT Defenses
- Dealing with Advanced Persistent Threats
- The Equation Group
- Key Tools Used in APT
- Dealing with Risks
- Risk Assessment to Protect Assets
- APT Checklists
- Course Summary
Information Security: NACs & Gateways
Course: 38 Minutes
- Course Overview
- BYOD and IoT Security Risks
- Challenges with BYOD
- NAC and Its Importance
- NAC Architecture
- Features of NAC
- Impact of Improperly Configured NAC
- NAC Elements
- Best Practices of Implementing NAC
- NAC Security Checklist
- NAC Authentication Methods
- Course Summary
Information Security: Subnetting & DNS for Security Architects
Course: 1 Hour, 6 Minutes
- Course Overview
- Subnetting and its Advantages
- The CIDR Notation
- Tips and Tricks in Subnetting
- VMs and Containers
- Deployment Considerations for VMs and Containers
- Best Practices for Deploying VMs
- Best Practices for VM and Container Security
- Types of DNS Attacks and their Mitigations
- Types of Subnetting Attacks and Mitigations
- Course Summary
Information Security: Securing Networking Protocols
Course: 57 Minutes
- Course Overview
- Common Protocols
- Security Issues of TCP/IP Model
- Threats, Vulnerabilities, and Mitigation
- Weak Protocols and Their Replacements
- Types of Security Protocols
- Uses of Security Protocols
- Importance of Security Protocols
- The Security-First Mindset
- Course Summary
Information Security: Hardened Security Topologies
Course: 43 Minutes
- Course Overview
- Security Topologies Introduction
- Designing Goals for Security Topology
- Advantages and Disadvantages of Security Topologies
- Impact of Integrating Cloud Topologies
- Layers of Security in Cloud Computing
- Methods to Harden Security Topologies
- Course Summary
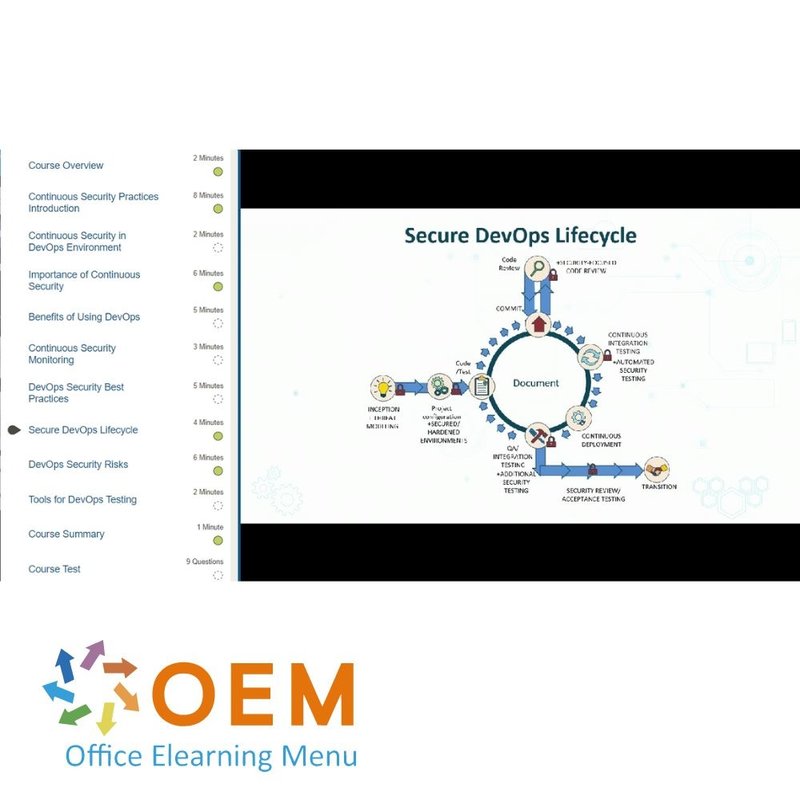
Information Security: Continual Infrastructure Testing
Course: 44 Minutes
- Course Overview
- Continuous Security Practices Introduction
- Continuous Security in DevOps Environment
- Importance of Continuous Security
- Benefits of Using DevOps
- Continuous Security Monitoring
- DevOps Security Best Practices
- Secure DevOps Lifecycle
- DevOps Security Risks
- Tools for DevOps Testing
- Course Summary
Information Security: Security Governance
Course: 1 Hour, 15 Minutes
- Course Overview
- Governance and Management Comparison
- Types of IT Governance Frameworks
- Senior Management Roles and Responsibilities
- Ensuring Good IT Security Governance
- Risks and Opportunities
- Security Governance Program
- Governance Framework Structure
- Course Summary
Information Security: Honeypots
Course: 36 Minutes
- Course Overview
- Honeypot Introduction
- Types of Honeypots
- Role of Honeypots in Security
- Disadvantages of a Honeypot
- Honeypot Uses
- Honeypot Deployment Strategies
- Available Honeypot Products
- Placement of Honeypot in a Network
- Install and Configure a Honeypot
- Honeypot Data Analysis
- Course Summary
Information Security: Pen Testing
Course: 1 Hour, 35 Minutes
- Course Overview
- Pen Testing Process Introduction
- Need for Pen Testing
- Pen Testing and Vulnerability Assessment
- Types of Pen Testing
- Pen Testing Weaknesses
- Types of Pen Testing Tools
- Target Selection for Pen Testing
- Threat Actors
- Types of Assets
- Types of Risk Responses
- Metasploit Framework
- MSFvenom
- Course Summary
Get started today!
✔️ Access anytime, anywhere to learn at your own pace.
✔️ Tests per chapter to track your progress and immediately test what you have learned.
✔️ Progress reports to gain insight into your learning progress.
Order your course now and start your journey in information security today!
| Language | English |
|---|---|
| Qualifications of the Instructor | Certified |
| Course Format and Length | Teaching videos with subtitles, interactive elements and assignments and tests |
| Lesson duration | 9 Hours |
| Progress monitoring | Yes |
| Access to Material | 365 days |
| Technical Requirements | Computer or mobile device, Stable internet connections Web browsersuch as Chrome, Firefox, Safari or Edge. |
| Support or Assistance | Helpdesk and online knowledge base 24/7 |
| Certification | Certificate of participation in PDF format |
| Price and costs | Course price at no extra cost |
| Cancellation policy and money-back guarantee | We assess this on a case-by-case basis |
| Award Winning E-learning | Yes |
| Tip! | Provide a quiet learning environment, time and motivation, audio equipment such as headphones or speakers for audio, account information such as login details to access the e-learning platform. |
There are no reviews written yet about this product.
OEM Office Elearning Menu Top 2 in ICT-trainingen 2024!
OEM Office Elearning Menu is trots op de tweede plaats in de categorie ICT-trainingen 2024 bij Beste Opleider van Nederland (Springest/Archipel). Dank aan al onze cursisten voor hun vertrouwen!
Reviews
There are no reviews written yet about this product.