Building a Security Toolbox Training


Building a Security Toolbox Training
Building a Security Toolbox E-Learning Training Gecertificeerde docenten Quizzen Assessments Tips Tricks Certificate.
Read more- Discounts:
-
- Buy 2 for €194,04 each and save 2%
- Buy 3 for €192,06 each and save 3%
- Buy 4 for €190,08 each and save 4%
- Buy 5 for €188,10 each and save 5%
- Buy 10 for €178,20 each and save 10%
- Buy 25 for €168,30 each and save 15%
- Buy 50 for €158,40 each and save 20%
- Availability:
- In stock
- Delivery time:
- Ordered before 5 p.m.! Start today.
- Award Winning E-learning
- Lowest price guarantee
- Personalized service by our expert team
- Pay safely online or by invoice
- Order and start within 24 hours
Building a Security Toolbox E-Learning
Build your ethical hacking toolkit and defend against modern cyber threats.
Organizations spend thousands on cybersecurity tools, but how can they be sure those assets are truly secure? One effective way is to use the same techniques as hackers — through ethical hacking and penetration testing. In this course, you’ll explore the history and purpose of security tools, how to use open-source intelligence (OSINT), and how to build a personal toolbox of ethical hacking tools to test and fortify your organization’s defenses.
This training is part of an Agile Learning Kit, giving you access to step-by-step e-learning, assessments, practice labs, mentor support, and 365 days of full access.
Why Choose This Training?
- Learn to build a practical and ethical security toolbox
- Explore tools for reconnaissance, vulnerability scanning, and network probing
- Understand the ethics and importance of penetration testing
- Categorize, select, and use the right tools for your security needs
- 365-day access to all resources, exams, labs, and mentoring included
Who Should Enroll?
This training is ideal for:
- Cybersecurity professionals and IT security specialists
- Ethical hackers and cybersecurity students
- Network administrators looking to identify vulnerabilities
- IT managers seeking insight into tool selection and usage for threat defense
This Learning Kit with more than 20 hours of learning is divided into three tracks:
Course content
SecOps Tool Landscape: Intro to Security Tools (SecTools)
Course: 1 Hour, 32 Minutes
- Course Overview
- Security Tools (SecTools)
- Categories of Security Tools
- Using Open-source Intelligence (OSINT) Tools
- Using a Password Cracker
- Security Tools Toolbox
- Ethical Hacking
- The Importance of Ethical Hacking
- Performing a Vulnerability Scan
- Using an Exploitation Tool
- The SecTools Environment
- How to Choose the Correct Security Tools
- Course Summary
SecOps Tool Landscape: The Kali Linux Security Platform
Course: 1 Hour, 22 Minutes
- Course Overview
- Kali Linux Features
- The Value of Kali Linux
- Reasons Not to Use Kali Linux
- Downloading Kali Linux
- Installing Kali Linux on a Virtual Machine
- Exploring the Kali Linux User Interface and Tools
- Installing Additional Tools in Kali Linux
- Performing a Port Scan Using Nmap
- Compromising a System with Hydra
- Performing a SQL Injection Attack Using sqlmap
- Cracking Passwords with Ophcrack
- Course Summary
SecOps Tools and 2021 Security Incidents: Microsoft Exchange Server Data Breach
Course: 1 Hour, 14 Minutes
- Course Overview
- Background of the MS Exchange Server Data Breach
- MS Exchange Server Data Breach Discovery
- How the Attack Was Disclosed Publicly
- What Was Compromised
- Tools for Detecting the Exploit
- Detecting Exploits Using Nmap
- Using Test-ProxyLogon.ps1 to Detect Vulnerability
- Using Metasploit to Exploit Vulnerability
- Patches and the Post-attack Response
- Course Summary
SecOps Tools and 2021 Security Incidents: Facebook Data Breach
Course: 54 Minutes
- Course Overview
- Background of the Facebook Data Breach
- How the Data Breach Was Discovered
- The Role of the Contact Importer Flaw
- The Use of Brute Forcing Tools
- Generating a Phone List Using Crunch
- Creating and Running a Web Scraper
- Phishing for Facebook Login Credentials
- Response: Facebook and the Cybersecurity Community
- Fallout from the Data Breach
- Course Summary
SecOps Tools and 2021 Security Incidents: Colonial Pipeline
Course: 1 Hour, 15 Minutes
- Course Overview
- Background of the Colonial Pipeline Breach
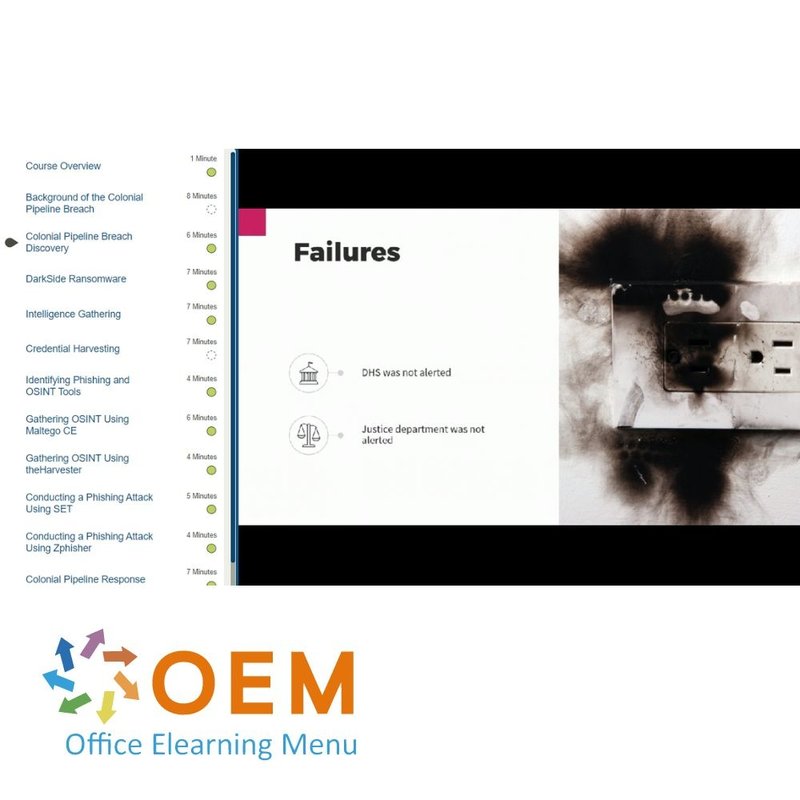
- Colonial Pipeline Breach Discovery
- DarkSide Ransomware
- Intelligence Gathering
- Credential Harvesting
- Identifying Phishing and OSINT Tools
- Gathering OSINT Using Maltego CE
- Gathering OSINT Using theHarvester
- Conducting a Phishing Attack Using SET
- Conducting a Phishing Attack Using Zphisher
- Colonial Pipeline Response
- Colonial Pipeline Fallout
- Course Summary
SecOps Tools and 2021 Security Incidents: JBS Ransomware Attack
Course: 1 Hour, 1 Minute
- Course Overview
- Background of the JBS Ransomware Attack
- Attack Discovery
- REvil Ransomware
- Vulnerability Scanning and Data Exfiltration Tools
- Scanning Domains Using Fierce
- Scanning for Vulnerabilities Using Nmap
- Scanning for Vulnerabilities Using Metasploit
- Exfiltrating Data From a Compromised Server
- JBS Ransomware Attack Recovery
- JBS Ransomware Attack Fallout
- Course Summary
SecOps Tools and 2021 Security Incidents: Kaseya Ransomware Attack
Course: 57 Minutes
- Course Overview
- Background of the Kaseya Ransomware Attack
- Kaseya Ransomware Attack Discovery
- Kaseya at the Center of a Supply Chain
- Tools Used for the Kaseya Ransomware Attack
- Detecting Privilege Escalation Vulnerabilities
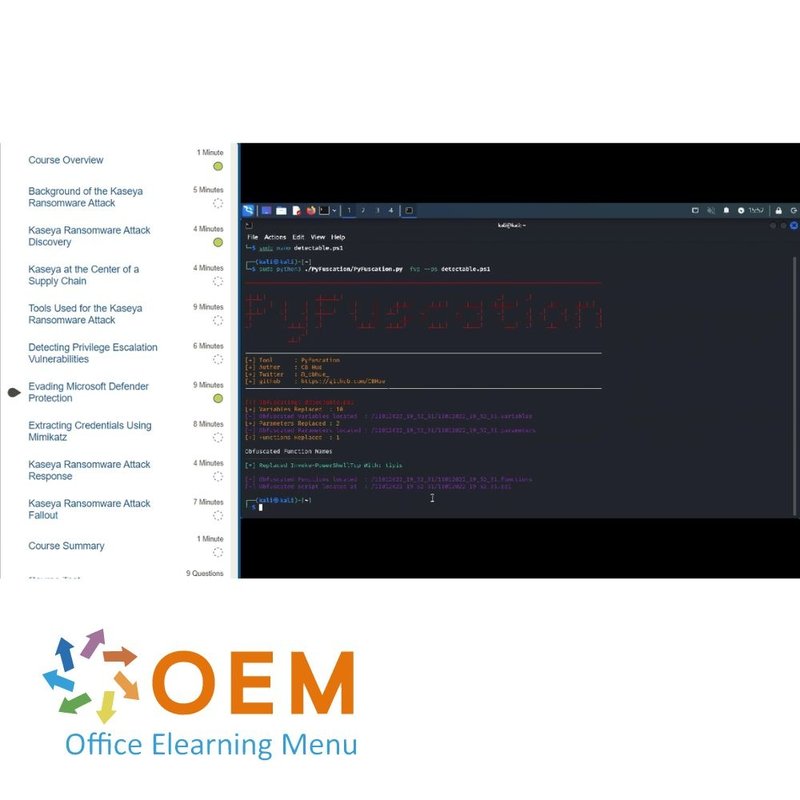
- Evading Microsoft Defender Protection
- Extracting Credentials Using Mimikatz
- Kaseya Ransomware Attack Response
- Kaseya Ransomware Attack Fallout
- Course Summary
SecOps Tools and 2021 Security Incidents: Log4Shell Exploit
Course: 1 Hour, 4 Minutes
- Course Overview
- Background of the Attack
- Attack Discovery
- Log4j Detection and Exploitation Tools
- Scanning for Log4Shell with Metasploit
- Scanning for Log4Shell with Targeted Scan Tools
- Configuring and Running Netcat Listener
- Distributing Files with Python Web Server
- Exploiting Log4Shell to Get a Reverse Shell
- Patches and Response
- Log4j Fallout
- Course Summary
Exploring SecOps Tools: Web Application Hardening via Burp Suite
Course: 1 Hour, 25 Minutes
- Course Overview
- Burp Suite
- Burp Suite Solutions
- DevSecOps Software
- Burp Suite Limitations
- Installing Burp Suite
- Navigating the Burp Suite User Interface
- Performing API Security Testing with Burp Suite
- Scanning a Website for Vulnerabilities
- Course Summary
Exploring SecOps Tools: Network Scanning Using Nmap
Course: 58 Minutes
- Course Overview
- The History of Network Mapper (Nmap)
- Nmap Features
- Nmap Limitations
- Installing Nmap
- Performing an Nmap TCP Connect Scan
- Performing an Nmap Stealth Scan
- Performing an Nmap Inverse TCP Scan
- Performing an Nmap ACK Scans
- Course Summary
Exploring SecOps Tools: Network Packet Manipulation Using Wireshark
Course: 59 Minutes
- Course Overview
- Wireshark Network Packet Analyzer
- Common Wireshark Use Cases
- Wireshark Limitations
- Installing Wireshark
- Filtering Network Traffic Using Wireshark
- Baselining in Wireshark
- Creating Rules in Wireshark
- Tunneling Remotely Using Wireshark
- Course Summary
Exploring SecOps Tools: Penetration Testing Using Metasploit Framework
Course: 1 Hour, 8 Minutes
- Course Overview
- Getting Started with Metasploit
- Metasploit Modules
- Metasploit Advantages and Disadvantages
- Installing Metasploit
- Discovery Scans
- Working With Modules, Exploits, and Payloads
- Exploring Common Metasploit Commands
- Attacking Systems Using Metasploit
- Course Summary
Exploring SecOps Tools: Using the Aircrack-ng Suite of Tools
Course: 1 Hour, 1 Minute
- Course Overview
- Aircrack-ng Suite of Tools
- Components of Aircrack-ng
- Aircrack-ng Alternatives
- Installing Aircrack-ng
- Driver Installation
- Using Aircrack-ng
- Cracking Passwords
- Aircrack-ng Common Options
- Course Summary
Exploring SecOps Tools: Port Scanning with Netcat
Course: 1 Hour, 4 Minutes
- Course Overview
- The Netcat Utility
- Installing Netcat
- Common Netcat Options
- Performing Basic Netcat Operations
- Netcat Penetration Testing Features
- Executing Basic Netcat Commands
- Performing Port Scans with Netcat Commands
- Using TCP Server and Client Commands
- Course Summary
Exploring SecOps Tools: Securing Passwords with hashcat
Course: 1 Hour, 9 Minutes
- Course Overview
- hashcat Suite of Tools
- hashcat Features
- Password Hashes
- Core Attack Modes
- Installing hashcat
- Cracking Passwords with hashcat
- Attacking with Rules and Toggling
- Password Cracking Systems
- Demonstrating WPA2 Vulnerabilities
- Course Summary
Exploring SecOps Tools: SQL Injection Testing Using sqlmap
Course: 48 Minutes
- Course Overview
- History of sqlmap
- sqlmap Features
- sqlmap Use Cases
- sqlmap and SQL Injection Techniques
- Installing sqlmap
- sqlmap Dependencies
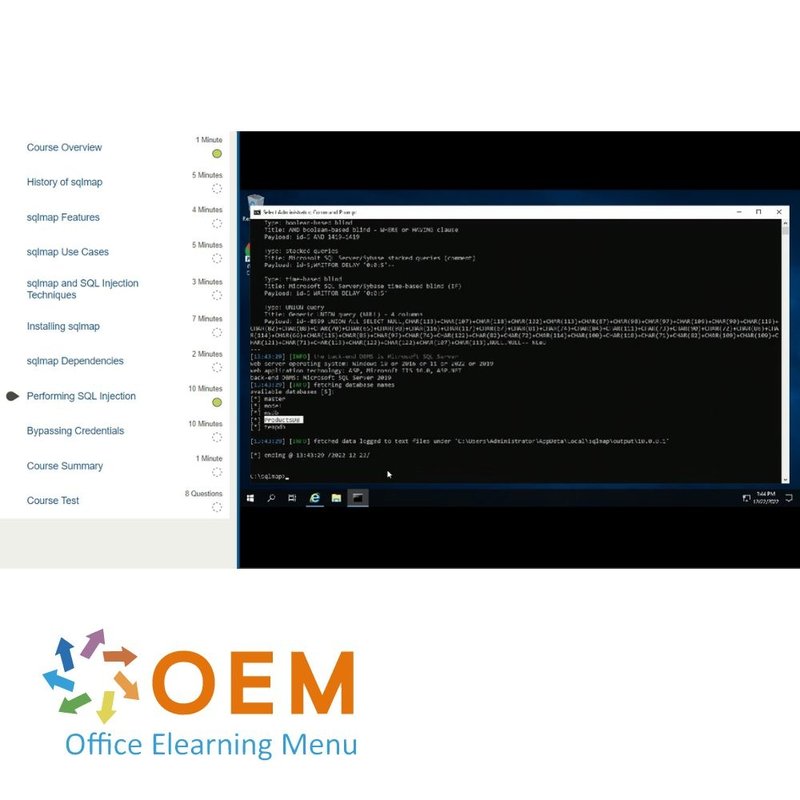
- Performing SQL Injection
- Bypassing Credentials
- Course Summary
Exploring SecOps Tools: Digital Forensic Collection with Autopsy
Course: 48 Minutes
- Course Overview
- Autopsy Forensics
- Autopsy Features
- Autopsy Input Formats and Reporting
- Installing Autopsy
- Autopsy Add-on Modules
- Configuring Autopsy
- Creating a Case in Autopsy
- Adding Data Sources in Autopsy
- Course Summary
Exploring SecOps Tools: Using the Social-Engineer Toolkit
Course: 57 Minutes
- Course Overview
- Social-Engineer Toolkit (SET)
- Social-Engineer Toolkit Features
- Social-Engineer Toolkit Attack Vectors
- Installing the Social-Engineer Toolkit
- Using the SET Spear Phishing Module
- Utilizing Website Attack Vectors
- Performing a Credential Harvester Attack
- Course Summary
SecOps Tools: The Role of AI in SecOps
Course: 1 Hour, 9 Minutes
- Course Overview
- Artificial Intelligence
- The History of Artificial Intelligence
- Artificial Intelligence Benefits
- Components of Artificial Intelligence
- The Application of Artificial Intelligence
- Common Artificial Intelligence Principles
- Security Threats Facing Artificial Intelligence
- Artificial Intelligence and SecOps
- Artificial Intelligence SecOps Tools
- Machine Learning Tools
- Course Summary
Assessment:
- Final Exam: SecOps Tools Proficienc
| Language | English |
|---|---|
| Qualifications of the Instructor | Certified |
| Course Format and Length | Teaching videos with subtitles, interactive elements and assignments and tests |
| Lesson duration | 20 Hours |
| Assesments | The assessment tests your knowledge and application skills of the topics in the learning pathway. It is available 365 days after activation. |
| Online Virtuele labs | Receive 12 months of access to virtual labs corresponding to traditional course configuration. Active for 365 days after activation, availability varies by Training |
| Online mentor | You will have 24/7 access to an online mentor for all your specific technical questions on the study topic. The online mentor is available 365 days after activation, depending on the chosen Learning Kit. |
| Progress monitoring | Yes |
| Access to Material | 365 days |
| Technical Requirements | Computer or mobile device, Stable internet connections Web browsersuch as Chrome, Firefox, Safari or Edge. |
| Support or Assistance | Helpdesk and online knowledge base 24/7 |
| Certification | Certificate of participation in PDF format |
| Price and costs | Course price at no extra cost |
| Cancellation policy and money-back guarantee | We assess this on a case-by-case basis |
| Award Winning E-learning | Yes |
| Tip! | Provide a quiet learning environment, time and motivation, audio equipment such as headphones or speakers for audio, account information such as login details to access the e-learning platform. |
There are no reviews written yet about this product.
OEM Office Elearning Menu Top 2 in ICT-trainingen 2024!
OEM Office Elearning Menu is trots op de tweede plaats in de categorie ICT-trainingen 2024 bij Beste Opleider van Nederland (Springest/Archipel). Dank aan al onze cursisten voor hun vertrouwen!
Reviews
There are no reviews written yet about this product.