Cybersecurity Essentials Training


Cybersecurity Essentials Training
Cybersecurity Essentials E-Learning Training Gecertificeerde docenten Quizzen Assessments test examen Live Labs Tips trucs Certificaat.
Lees meer- Kortingen:
-
- Koop 2 voor €390,04 per stuk en bespaar 2%
- Koop 3 voor €386,06 per stuk en bespaar 3%
- Koop 4 voor €382,08 per stuk en bespaar 4%
- Koop 5 voor €378,10 per stuk en bespaar 5%
- Koop 10 voor €358,20 per stuk en bespaar 10%
- Koop 25 voor €338,30 per stuk en bespaar 15%
- Koop 50 voor €318,40 per stuk en bespaar 20%
- Beschikbaarheid:
- Op voorraad
- Levertijd:
- Voor 17:00 uur besteld! Start vandaag. Gratis Verzending.
- Award Winning E-learning
- De laagste prijs garantie
- Persoonlijke service van ons deskundige team
- Betaal veilig online of op factuur
- Bestel en start binnen 24 uur
Cybersecurity Essentials E-Learning Training
Bescherm je organisatie tegen digitale dreigingen – begin met de basis van cybersecurity.
In een tijdperk waarin informatie de nieuwe brandstof van organisaties is, wordt cybersecurity steeds belangrijker. Deze training helpt je om inzicht te krijgen in actuele beveiligingsrisico's en de stappen die nodig zijn om je organisatie te beschermen tegen misbruik, datalekken en cyberaanvallen.
Wat je leert:
- Inzicht in veelvoorkomende cyberdreigingen en hun impact op bedrijven
- Leren hoe je beveiligingsrisico’s identificeert, evalueert en beperkt
- Richtlijnen en best practices toepassen voor risicobeheersing
- Basisprincipes van informatiebeveiliging en compliance
- Cyberbewustzijn ontwikkelen als eerste verdedigingslinie
Deze training maakt deel uit van een Agile Learning Kit en bevat assessments, labs, e-learningmodules en 365 dagen toegang tot alle materialen.
Waarom kiezen voor deze opleiding?
- Begrijp en herken digitale dreigingen in een zakelijke context
- Krijg een solide basis in IT-beveiliging, zonder diep technische voorkennis
- Leer de fundamenten van risk management en beveiligingsbeleid
- Inclusief mentorbegeleiding, praktijklabs en e-learning
- 365 dagen toegang tot alle leermiddelen in jouw eigen tempo
Wie zou moeten deelnemen?
Deze training is ideaal voor:
- IT-professionals die starten met cybersecurity
- Managers en teamleiders die verantwoordelijk zijn voor dataveiligheid
- Studenten en zij-instromers die de basis van cyberveiligheid willen leren
- Iedereen in een organisatie die betrokken is bij digitale processen
Deze Learning Kit, met meer dan 35 uur online content, is onderverdeeld in de volgende tracks:
Demo Cybersecurity Essentials Training
Cursusinhoud
Track 1: Becoming Security Aware
Track 2: Evaluating and Planning for Security Risks
Track 3: Mitigating Security Risks
Track 1: Becoming Security Aware
In this track, the focus will be on cybersecurity awareness.
Content:
E-learning
Cybersecurity Awareness: Getting Started with Security Foundations
Course: 1 Hour, 15 Minutes
- Course Overview
- The Foundational Concepts of Information Security
- Information Security Roles in an Organization
- The Duties of Various Information Security Roles
- Security-related User and Organization Expectations
- The RACI Chart for Distinguishing Security Roles
- Strategic Planning and Decision-making in Security
- Importance of Communication in Information Security
- The Concept of Security Governance
- Information Security Governance Activities
- Information Security and Meeting Business Goals
- Course Summary
Cybersecurity Awareness: Information Security Fundamentals
Course: 1 Hour, 55 Minutes
- Course Overview
- Information Security Foundations Recap
- The Consequences of Poor Information Security
- The Numerous Domains of Information Security
- Cybersecurity as a Domain of Information Security
- Types of Cybersecurity Approaches
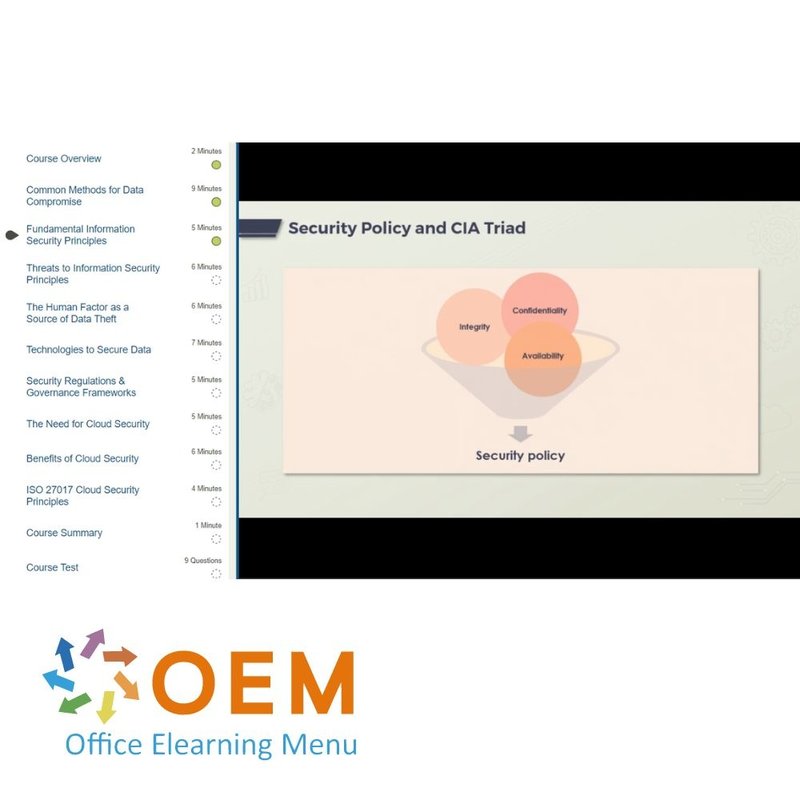
- The CIA Triad – Confidentiality
- The CIA Triad – Integrity
- The CIA Triad – Availability
- CIA Impacts and Methods
- Security Architecture Frameworks
- The Concept of Security Controls
- Security Control Categories, Types, and Examples
- Examples of Risk in Daily Life and Security
- The Role of Humans in Information Security
- Course Summary
Cybersecurity Awareness: Key Security Terms & Concepts
Course: 2 Hours, 21 Minutes
- Course Overview
- Cybersecurity Assets and Risks
- Cybersecurity Threats
- Cybersecurity Vulnerability and Countermeasures
- Types of Threat Actors in Cybersecurity
- Types of Attack Targets in Cybersecurity
- Security Threat, Risk, and Exposure
- Types of Security Threats
- Mobile Technology Threats
- Cloud Threat Definition and Types
- Defining Advanced Persistent Threats (APTs)
- Examples of Advanced Persistent Threats (APTs)
- Insider Threat in an Organization
- Malware Definition and Types
- Steps in a Security Attack
- Defining Uncertainty in Security
- Course Summary
Cybersecurity Awareness: Exposure to Security Risks
Course: 1 Hour, 39 Minutes
- Course Overview
- Primary Information Security Issues
- Foremost Security Threats to an Organization
- Examples of Threats, Risks, and Exposure
- How Exposure to Security Risks Occur
- The Importance of Threat Identification
- The STRIDE Model for Threat Identification
- The PASTA Threat Model and Its Stages
- Placing Responsibility for Security
- Methods to Reduce Security Risks
- Course Summary
Final Exam assessment:
Estimated duration: 90 minutes
Track 2: Evaluating and Planning for Security Risks
In this track, the focus will be on security risks. Explore risk identification, risk assessments, and risk management.
Content:
E-learning
Security Risks: Key Risk Terms & Concepts
Course: 1 Hour, 53 Minutes
- Course Overview
- Relationship between Security Risks and Assets
- Likelihood versus Probability
- Vulnerabilities, Threats and Risks
- Risk Probability, Impact and Risk Score
- Elements of Risk Severity
- Risk Appetite versus Risk Tolerance
- Advantages of a Risk Management Process
- Components of a Risk Management Plan
- Risk Management Using a Risk Register
- Risk Treatment Methods
- Importance of Risk Management
- Frameworks and Standards for Risk Management
- Stages in the Security Risk Management Process
- Security Risk Assessment
- Course Summary
Security Risks: Performing Security Risk Identification
Course: 58 Minutes
- Course Overview
- Relationship between Security Threat and Risk
- Importance of Security Risk Identification
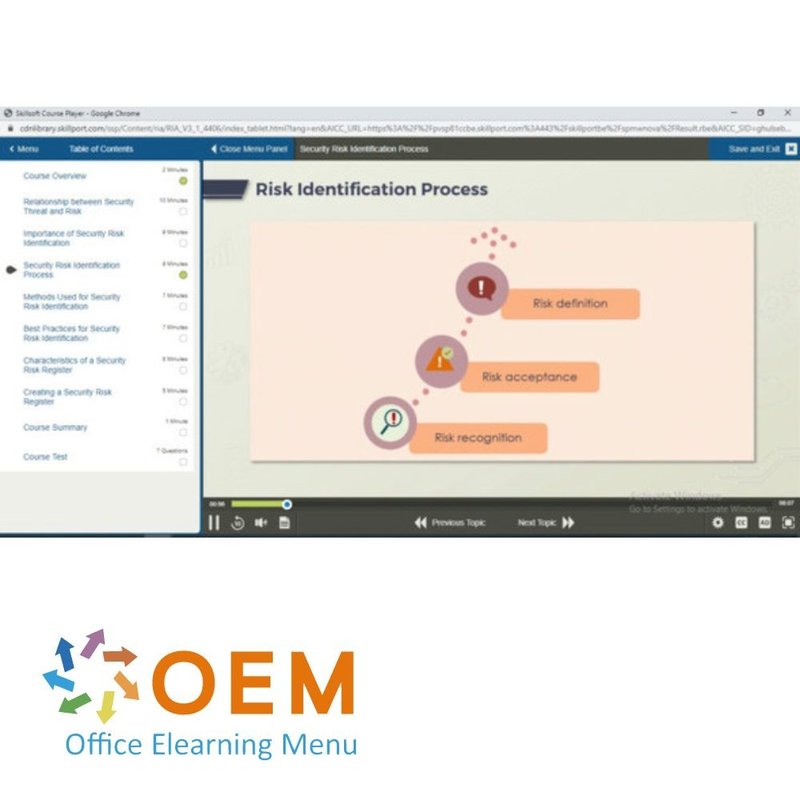
- Security Risk Identification Process
- Methods Used for Security Risk Identification
- Best Practices for Security Risk Identification
- Characteristics of a Security Risk Register
- Creating a Security Risk Register
- Course Summary
Security Risks: Performing Security Risk Assessments
Course: 1 Hour, 37 Minutes
- Course Overview
- Features and Benefits of Security Risk Assessment
- Types of Security Risk Assessment
- Characteristics of Qualitative Risk Assessment
- Characteristics of Quantitative Risk Assessment
- Security Risk Assessment Methods
- Assessing Security Vulnerability
- Categorizing Risk Using Four-quadrant Classification
- Updating a Security Risk Register in Microsoft Excel
- Security Risk Prioritization
- Probability-impact Matrix for Risk Prioritization
- Illustrating the Probability-impact Matrix
Course Summary
Security Risks: Planning for Security Risk Management
Course: 1 Hour, 27 Minutes
- Course Overview
- Importance of Risk Management and Best Practices
- Stages in a Security Risk Management Process
- Security Risk Management Plan and Risk Categories
- Components of a Security Risk Management Plan
- Features of a Security Risk Mitigation Plan
- Creating a Risk Mitigation Plan in Microsoft Word
- Risk Tolerance and Risk Appetite
- Security Risk Monitoring and Control Measures
- Security Risk Strategies Methods
- Role of Decision Making in Managing Security Risks
- Course Summary
Final Exam assessment:
Estimated duration: 90 minutes
Practice Lab: Evaluating and Planning for Security Risks
Practice evaluating and planning for security risks by creating a risk register and identifying risks, applying a probability matrix to identify high risks, performing a vulnerability assessment and creating a risk mitigation plan.
Track 3: Mitigating Security Risks
In this track, the focus will be on mitigating security risks. Explore how to manage and maintain different types of risks such as network, physical, social engineering, and cloud risks.
Content:
E-learning
Mitigating Security Risks: Managing Network & Infrastructure Security Risks
Course: 1 Hour, 33 Minutes
- Course Overview
- Network Vulnerabilities as Threats
- Network Vulnerability Prevention Methods
- Examples of Network Vulnerabilities
- The Purpose of Network Security
- Network Zones and Security
- Monitoring, Detection, and Logging
- Tools for Monitoring, Detection, and Logging
- Characteristics of a Secure Network Design
- Guidelines and Best Practices for Network Security
- Course Summary
Mitigating Security Risks: Managing Physical Security Risks
Course: 57 Minutes
- Course Overview
- Physical Security Risks
- How Tailgating Works
- Physical Security and its Importance
- Layers of Physical Security
- Best Practices for Physical Security
- Security Principles for Site and Facility
- Tightening Facility and Site Security
- Internal and External Security Controls
- Physical Security Standards
- Course Summary
Mitigating Security Risks: Cyber Security Risks
Course: 1 Hour, 17 Minutes
- Course Overview
- The Core Facets of Security Risks
- Information and Data Security Risks
- Cloud Security Risks
- Sources of Cybercrimes and Attacks
- Examples of Cyber Attacks and Crimes
- Malware Handling Best Practices
- Handling DoS and DDoS Attacks
- Handling Backdoor Attacks
- The Role of Zero-Day (0day) Exploits
- Key Examples of Zero-Day Attacks
- Handling Zero-Day Vulnerabilities
- Course Summary
Mitigating Security Risks: Managing Social Engineering Risks
Course: 1 Hour, 13 Minutes
- Course Overview
- Social Engineering Explained
- The Intents of Social Engineering
- Principles of Social Engineering
- Social Engineering as the Attack Tool
- Types of Social Engineering Attacks
- Types of Spoofing Attacks
- Possible Targets in Social Engineering
- Best Practices for Handling Social Engineering
- Course Summary
Mitigating Security Risks: Information, Cloud, & Data Security Risk Considerations
Course: 56 Minutes
- Course Overview
- Common Methods for Data Compromise
- Fundamental Information Security Principles
- Threats to Information Security Principles
- The Human Factor as a Source of Data Theft
- Technologies to Secure Data
- Security Regulations & Governance Frameworks
- The Need for Cloud Security
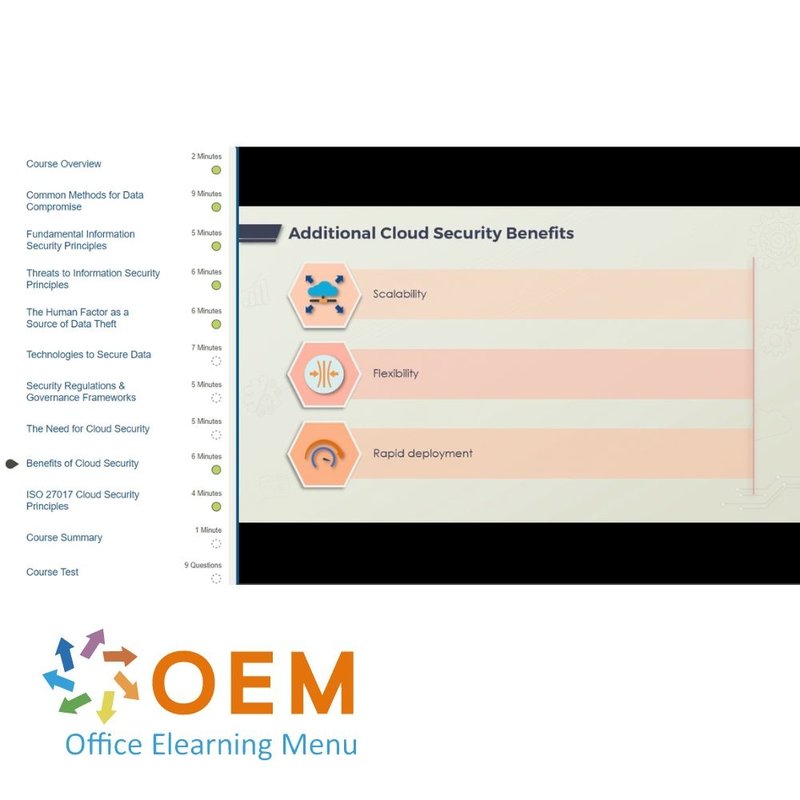
- Benefits of Cloud Security
- ISO 27017 Cloud Security Principles
- Course Summary
Mitigating Security Risks: Managing Information, Cloud, & Data Security Risks
Course: 1 Hour, 30 Minutes
- Course Overview
- Common Methods for Data Compromise
- Fundamental Information Security Principles
- Threats to Information Security Principles
- The Human Factor as a Source of Data Theft
- Technologies to Secure Data
- Security Regulations & Governance Frameworks
- The Need for Cloud Security
- Benefits of Cloud Security
- ISO 27017 Cloud Security Principles
- Course Summary
Mitigating Security Risks: Handling Natural Threats
Course: 34 Minutes
- Course Overview
- Securing against Natural Disasters
- Considerations for Natural Disaster Risk Mitigation
- The Composition of an Emergency Action Plan
- Natural Disaster Emergency Action Plan Effectiveness
- Drafting an Emergency Action Plan
- Course Summary
Mitigating Security Risks: Managing Risks from Internal Stakeholders
Course: 50 Minutes
- Course Overview
- The Role of Internal Stakeholders in Security
- Security Risks from Stakeholders
- The Role of Effective Communication in Security
- Methods in Effective Reporting of Security Health
- Communication for a Secure Workplace
- Course Summary
Mitigating Security Risks: Managing Security in a Hybrid Workplace
Course: 53 Minutes
- Course Overview
- Hybrid Workplaces Explained
- Hybrid Workplace Security Concerns
- Security Decisions for Hybrid Workplaces
- The Concept of 'Work from Home' (WFH)
- The Security Concerns of 'Work from Home'
- 'Work from Home' (WFH) vs. Hybrid Workplaces
- Work from Home Security: Responsibility Delegation
- Work from Home (WFH) Security Guidelines
- Course Summary
Mitigating Security Risks: Information Security Governance
Course: 1 Hour, 24 Minutes
- Course Overview
- Information Security Governance
- The Need for Security Governance
- The Benefits of Security Governance
- Security Governance and the CIA Triad
- Security Governance Outcomes
- Security Governance vs. Security Management
- The Elements of Security Governance
- The Role of a Security Policy
- IT Governance Frameworks
- The Role of Senior Management in Security Governance
- Methods to Create and Deliver Governance
- Senior Management Roles and Responsibilities
- Methods to Review Governance
- Signs of Security Governance
- Missing Security Governance
- Reasons for Ineffective Security Governance
- Methods to Implement Security Governance
- The Security Governance Structure
- Course Summary
Mitigating Security Risks: Managing the Incidents
Course: 1 Hour, 9 Minutes
- Course Overview
- Security Breach Incidents: Definition and Examples
- The Incident Management Process
- Incident Management Process Key Terms
- The Need for an Incident Management Process
- Incident Management Process Benefits
- Incident Management Process Steps
- Incident Management: Dependencies on Other Processes
- Incident Management Roles and Responsibilities
- Using Incident Management Forms
- Measures to Prevent Incidents
- Signs of a Security Incident
- Course Summary
Mitigating Security Risks: Maintaining Business Continuity
Course: 1 Hour, 38 Minutes
- Course Overview
- Business Continuity Planning for Threat Management
- The Role of Disaster Recovery Planning
- Business Continuity vs. Disaster Recovery Planning
- Business Continuity Planning's Role in Disasters
- Business Continuity Planning: The Core Steps
- The Role of the Risk Management Plan
- The Role of Business Impact Analysis (BIA)
- The Role of the Incident Response Plan
- The Role of Recovery Time Objectives (RTOs)
- The Role of Recovery Point Objectives (RPOs)
- The Role of the Disaster Recovery Plan
- Business Continuity vs. Emergency Action Plans
- Organizational Post-disaster Recovery Planning
- Building Business Resiliency During Disasters
- Pursuing Business Excellence during a Pandemic
- Course Summary
Mitigating Security Risks: Maintaining a Secure Workplace
Course: 51 Minutes
- Course Overview
- The Need for a Secure Workplace
- Best Practices for a Secure Workplace
- Best Practices for Developing a Security Policy
- Implementing Security Training and Awareness
- Guidelines for Cultivating a Security Mindset
- Security Buy-in: Employee Encouragement Techniques
- The Role of the Cyber Maturity Model Certification
- Course Summary
Final Exam assessment:
Estimated duration: 90 minutes
Practice Lab: Mitigating Security Risks
Mitigate security risks by identifying a phishing email, creating and sending a phishing email and subscribing to the Microsoft Security Notification Service. Then, calculate the vulnerability score for a given vulnerability.
| Taal | Engels |
|---|---|
| Kwalificaties van de Instructeur | Gecertificeerd |
| Cursusformaat en Lengte | Lesvideo's met ondertiteling, interactieve elementen en opdrachten en testen |
| Lesduur | 35 uur |
| Assesments | De assessment test uw kennis en toepassingsvaardigheden van de onderwerpen uit het leertraject. Deze is 365 dagen beschikbaar na activering. |
| Online Virtuele labs | Ontvang 12 maanden toegang tot virtuele labs die overeenkomen met de traditionele cursusconfiguratie. Actief voor 365 dagen na activering, beschikbaarheid varieert per Training. |
| Online mentor | U heeft 24/7 toegang tot een online mentor voor al uw specifieke technische vragen over het studieonderwerp. De online mentor is 365 dagen beschikbaar na activering, afhankelijk van de gekozen Learning Kit. |
| Voortgangsbewaking | Ja |
| Toegang tot Materiaal | 365 dagen |
| Technische Vereisten | Computer of mobiel apparaat, Stabiele internetverbindingen Webbrowserzoals Chrome, Firefox, Safari of Edge. |
| Support of Ondersteuning | Helpdesk en online kennisbank 24/7 |
| Certificering | Certificaat van deelname in PDF formaat |
| Prijs en Kosten | Cursusprijs zonder extra kosten |
| Annuleringsbeleid en Geld-Terug-Garantie | Wij beoordelen dit per situatie |
| Award Winning E-learning | Ja |
| Tip! | Zorg voor een rustige leeromgeving, tijd en motivatie, audioapparatuur zoals een koptelefoon of luidsprekers voor audio, accountinformatie zoals inloggegevens voor toegang tot het e-learning platform. |
Er zijn nog geen reviews geschreven over dit product.
OEM Office Elearning Menu Top 2 in ICT-trainingen 2024!
OEM Office Elearning Menu is trots op de tweede plaats in de categorie ICT-trainingen 2024 bij Beste Opleider van Nederland (Springest/Archipel). Dank aan al onze cursisten voor hun vertrouwen!
Beoordelingen
Er zijn nog geen reviews geschreven over dit product.