Certified Information Security Manager CISM Training



Certified Information Security Manager CISM Training
Certified Information Security Manager CISM - Online E-Learning Training. Bestellen en direct starten voor de beste prijs.
Lees meer- Merk:
- ISACA
- Kortingen:
-
- Koop 2 voor €351,82 per stuk en bespaar 2%
- Koop 3 voor €348,23 per stuk en bespaar 3%
- Koop 4 voor €344,64 per stuk en bespaar 4%
- Koop 5 voor €341,05 per stuk en bespaar 5%
- Koop 10 voor €323,10 per stuk en bespaar 10%
- Koop 25 voor €305,15 per stuk en bespaar 15%
- Koop 50 voor €287,20 per stuk en bespaar 20%
- Beschikbaarheid:
- Op voorraad
- Levertijd:
- Voor 17:00 uur besteld! Start vandaag. Gratis Verzending.
- Award Winning E-learning
- De laagste prijs garantie
- Persoonlijke service van ons deskundige team
- Betaal veilig online of op factuur
- Bestel en start binnen 24 uur
Certified Information Security Manager CISM E-Learning Training
Beheer, ontwerp, beoordeel en overzie informatiebeveiliging op ondernemingsniveau — bereid u voor op de internationaal erkende CISM-certificering.
De Certified Information Security Manager (CISM)-cursus is speciaal ontwikkeld voor professionals die verantwoordelijk zijn voor het beheren, ontwerpen, toezicht houden op en evalueren van de informatiebeveiligingsfunctie binnen een organisatie.
Deze training is ideaal voor ervaren securitymanagers, consultants en IT-auditors die hun strategische en beleidsmatige vaardigheden willen versterken op het gebied van informatiebeveiliging.
Toelatingseisen:
Minimaal vijf (5) jaar ervaring in informatiebeveiligingsmanagement.
Vrijstellingen zijn mogelijk voor maximaal twee (2) jaar, afhankelijk van uw achtergrond.
ISACA® Certified
E-learning cursus (21+ uur) – inclusief interactieve modules, oefenexamens en begeleiding door een online mentor.
Demo Certified Information Security Manager CISM Training
Cursusinhoud
CISM 2022: Information Security Governance
Course: 1 Hour, 40 Minutes
- Course Overview
- Business Model for Information Security (BMIS)
- Asset Identification and Classification
- Supply Chain Security
- Personnel Management
- Information Security Programs
- Reviewing Service-level Agreements (SLAs)
- Change Management
- Configuration Management
- Organizational Security Policies
- IT Maturity Models
- Capital Versus Operating Expenses
- Chain of Custody
- Organizational Culture and Security
- Use of Control Objectives for Information Technologies (COBIT) for IT Governance
- Course Summary
CISM 2022: Business Continuity & Security
Course: 1 Hour, 13 Minutes
- Course Overview
- Business Continuity Plan (BCP) and Business Impact Analysis (BIA)
- Disaster Recovery Plan (DRP)
- Data Roles
- IT Security Roles
- Contractual Obligations
- Security Baselines
- Establishing a Performance Baseline on Windows Server
- Establishing a Performance Baseline in the Azure Cloud
- Physical Security
- Security Control Types
- Course Summary
CISM 2022: Incident Response
Course: 42 Minutes
- Course Overview
- Incident Response Plan (IRP)
- Incident Escalation
- Incident Eradication
- Incident Containment
- Post-incident Lessons Learned
- Automating Incident Response in the Cloud
- Course Summary
CISM 2022: Security Standards
Course: 53 Minutes
- Course Overview
- The European Union's General Data Protection Regulation (GDPR)
- ISO/IEC Standards
- America's Health Insurance Portability and Accountability Act (HIPAA)
- America's Federal Risk and Authorization Management Program (FedRamp)
- Payment Card Industry Data Security Standard (PCI DSS)
- Canada's Personal Information Protection and Electronic Documents Act (PIPEDA)
- China's Personal Information Protection Law (PIPL)
- Using the Cloud Controls Matrix (CCM)
- Course Summary
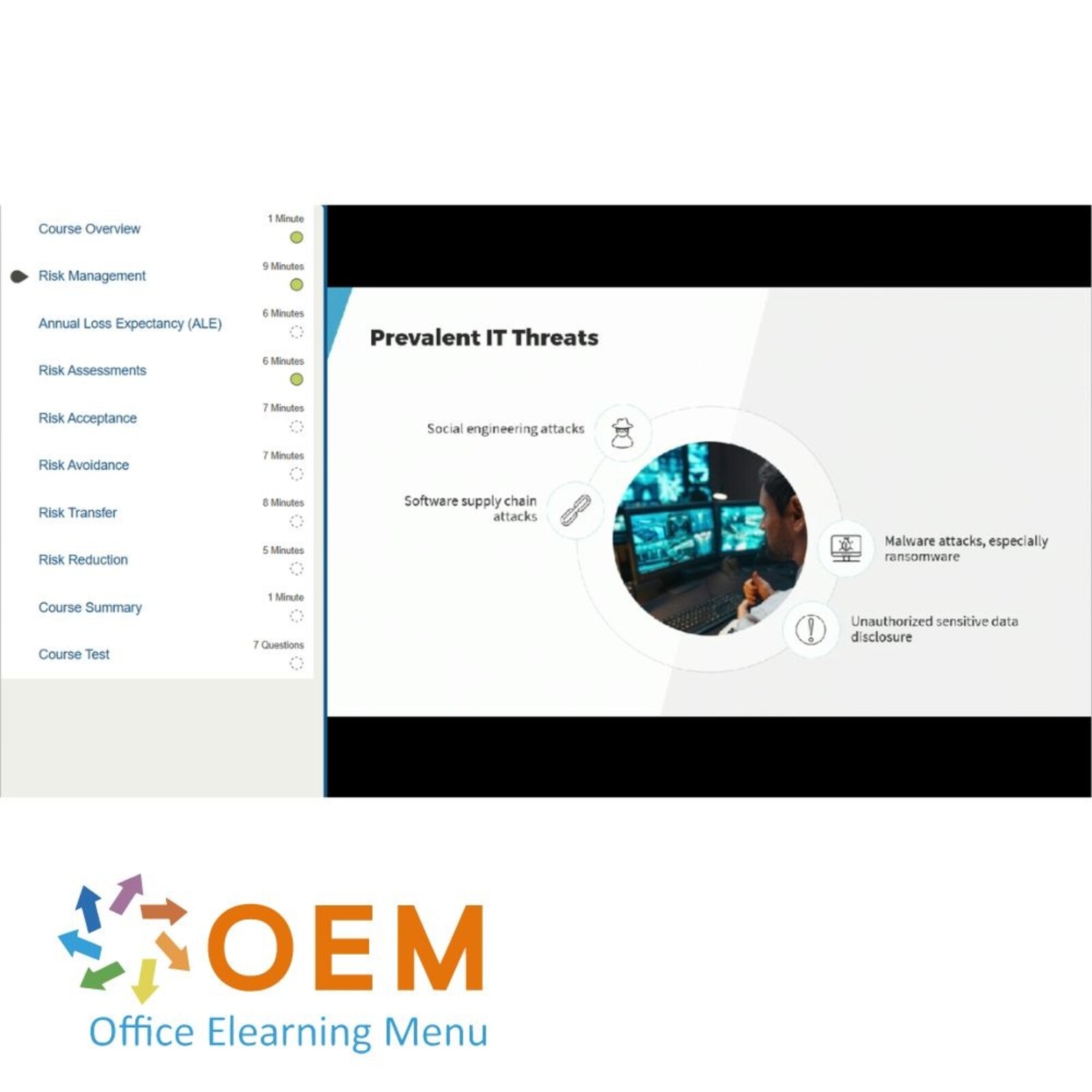
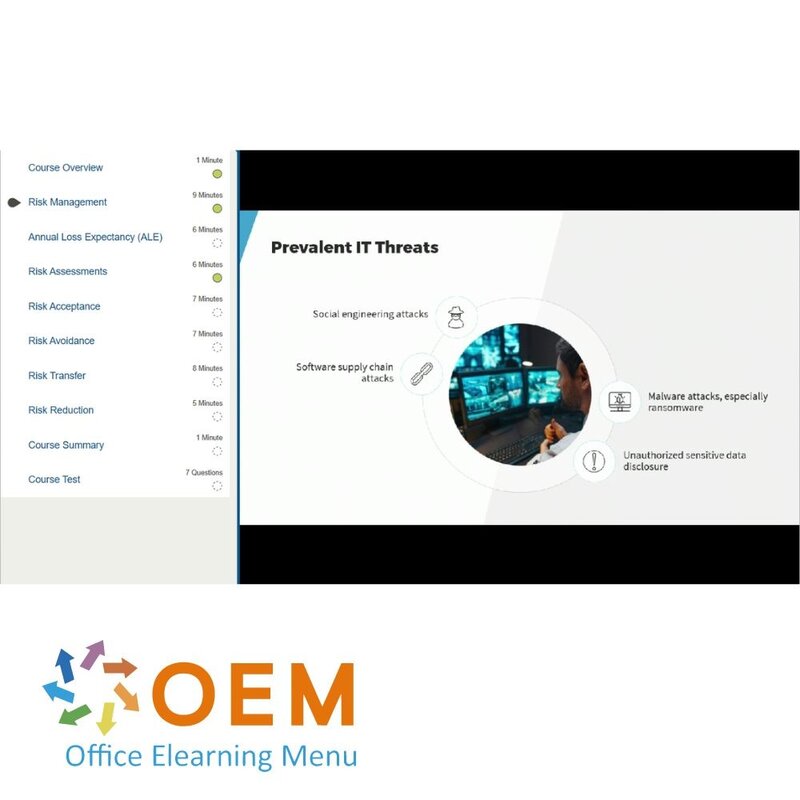
CISM 2022: Managing Risk
Course: 50 Minutes
- Course Overview
- Risk Management
- Annual Loss Expectancy (ALE)
- Risk Assessments
- Risk Acceptance
- Risk Avoidance
- Risk Transfer
- Risk Reduction
- Course Summary
CISM 2022: Data Privacy
Course: 57 Minutes
- Course Overview
- Personally Identifiable Information (PII)
- Data Residency
- Data Loss Prevention (DLP)
- Classifying Data with Amazon Macie
- Classifying Data with Microsoft Purview Governance
- Configuring Windows Server Data Classification
- Using Tags to Organize Cloud Resources
- Encrypting Cloud Storage
- Course Summary
CISM 2022: Assessing Risk
Course: 46 Minutes
- Course Overview
- Vulnerability Assessments
- Conducting a Network Vulnerability Assessment
- Scanning a Web Application For Vulnerabilities
- Perform a Gap Analysis
- Penetration Testing
- Viewing Cloud Resource Security Compliance
- Course Summary
CISM 2022: Managing Authentication
Course: 54 Minutes
- Course Overview
- Authentication
- Managing Amazon Web Services Users and Groups
- Managing Microsoft Azure Users and Groups
- Managing Linux Users and Groups
- Managing Windows Server Users and Groups
- Enabling Amazon Web Services IAM User MFA
- Managing Password Policies
- Identity Federation
- Course Summary
CISM 2022: Implementing Access Control
Course: 1 Hour, 2 Minutes
- Course Overview
- Authorization
- Access Control Models
- Configuring Windows Dynamic Access Control
- Administering ABAC through Azure Dynamic Groups
- Using Azure Permissions through RBAC
- Managing Windows File System Permissions
- Handling Linux File System Permissions
- Configuring Windows File System Auditing
- Using Active Directory Delegated Administration
- Course Summary
CISM 2022: Network Security
Course: 1 Hour, 11 Minutes
- Course Overview
- The OSI Model
- Network Switching and Network Access Control
- Creating a Virtualization Sandbox
- DHCP and DNS Security
- Implementing DHCP and DNS Security
- Wi-Fi Authentication Methods
- Honeypots and Honeynets
- Implementing a Honeypot
- Analyzing Captured Network Traffic
- Course Summary
CISM 2022: Network Attack Mitigation
Course: 1 Hour, 2 Minutes
- Course Overview
- Firewall Types
- Configuring Windows Defender Firewall
- Adjusting a Linux Firewall
- Manage Azure Network Security Groups (NSGs)
- Administering Microsoft Azure Firewall
- Proxy Servers
- Intrusion Detection and Prevention
- Configuring the Snort IDS Tool
- Course Summary
CISM 2022: IT Service & Data Availability
Course: 1 Hour, 17 Minutes
- Course Overview
- High Availability
- Load Balancing
- Configuring a Cloud-based Load Balancer
- Exploring Types of Data Backups
- Configuring Windows Server Backups
- Enabling Cloud Resource Backups
- Data Availability and RAID Levels
- Configure Software RAID on Windows
- Configure Software RAID on Linux
- Configuring Azure Storage Account Replication
- Enabling Azure Virtual Machine Replication
- Course Summary
CISM 2022: Common Network Security Threats
Course: 1 Hour, 15 Minutes
- Course Overview
- Threat Actor Types
- Viewing Common Vulnerabilities and Exposures (CVEs)
- Using the MITRE ATT&CK Knowledge Base
- OWASP Top 10 Web Application Attacks
- Working with Bug Bounties
- Common Wi-Fi Attacks
- SYN Flood Attacks
- Buffer Overflow Attacks
- Advanced Persistent Threat (APT)
- DDoS Attacks
- Using Internet User VPNs and the Tor Web Browser
- Course Summary
CISM 2022: Common Network Security Attacks
Course: 50 Minutes
- Course Overview
- Scanning Networks Using Nmap
- Compromising a Web Browser
- Executing a SQL Injection Attack
- Configuring a Reverse Shell
- Spoofing Network Traffic
- Executing a Distributed Denial-of-service (DDoS) Attack
- Brute Forcing Remote Desktop Protocol (RDP) Connections
- Course Summary
CISM 2022: Cloud Computing & Coding
Course: 50 Minutes
- Course Overview
- Cloud Computing Deployment Models
- Cloud Computing Service Model
- Cloud Computing and Security
- Deploying a Microsoft Azure Blueprint Environment
- The Software Development Life Cycle (SDLC)
- Secure Coding
- SecDevOps
- Course Summary
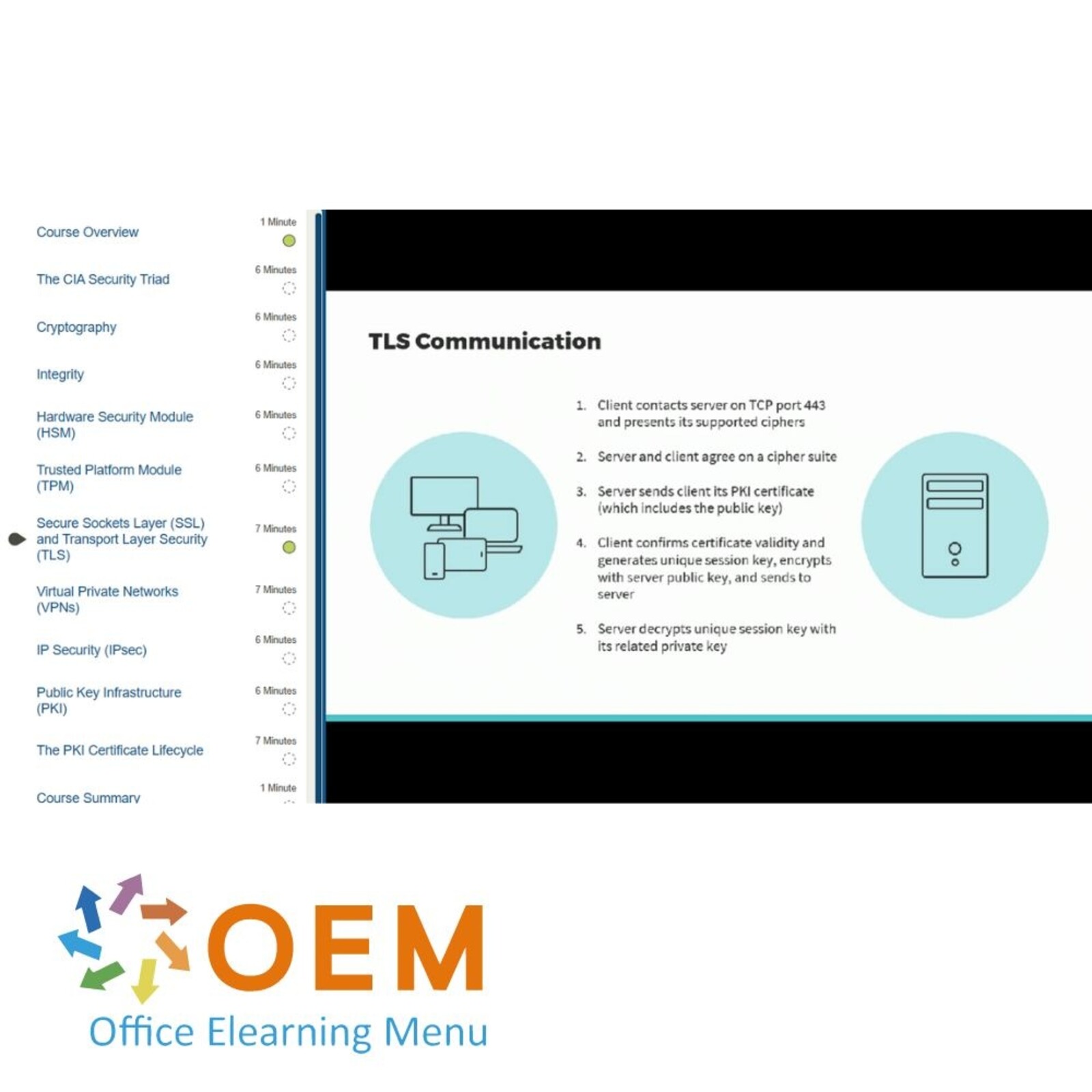
CISM 2022: Data Protection with Cryptography
Course: 1 Hour, 6 Minutes
- Course Overview
- The CIA Security Triad
- Cryptography
- Integrity
- Hardware Security Module (HSM)
- Trusted Platform Module (TPM)
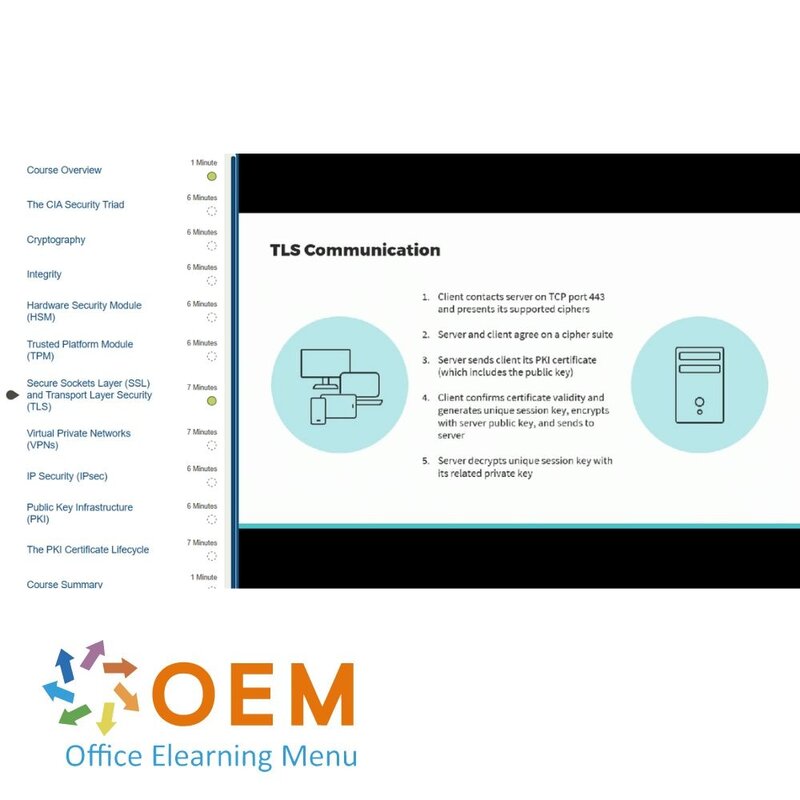
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
- Virtual Private Networks (VPNs)
- IP Security (IPsec)
- Public Key Infrastructure (PKI)
- The PKI Certificate Lifecycle
- Course Summary
CISM 2022: Applied Cryptography
Course: 1 Hour, 16 Minutes
- Course Overview
- Generating File System Hashes Using Linux
- Generating File System Hashes Using PowerShell
- Enabling an HTTPS Binding
- Deploying a Private Certificate Authority (CA)
- Managing PKI Certificate Templates
- Acquiring PKI Certificates
- Client PKI Certificates
- Managing Windows Encrypting File System (EFS)
- Managing Microsoft BitLocker
- Managing Linux File System Encryption
- Configuring a Cloud-based User VPN
- Implementing IPsec with Windows
- Course Summary
CISM 2022: Secure Device & OS Management
Course: 1 Hour, 39 Minutes
- Course Overview
- Mobile Device Security
- Mobile Device Remote Wipe
- Centrally Managing Devices
- Securely Wiping Storage Media
- Hardening Windows Stations Using Group Policy
- Disabling SSL on Windows Servers
- Digital Forensics Hardware and Software
- Storage Area Network (SAN) Security
- Implementing a Jump Box Solution
- Configuring Microsoft Azure Managed Identities
- Device and Operating System (OS) Hardening
- Hardening a Wi-Fi Router
- Hardening a Network Printer
- Firmware and Software Patching
- Course Summary
CISM 2022: Social Engineering & Malware
Course: 43 Minutes
- Course Overview
- Social Engineering
- Malware Types
- Reviewing Phishing Attack Email Messages
- Executing a Social Engineering Attack
- Configuring Endpoint Malware Solutions
- Analyzing Infected Files
- Course Summary
CISM 2022: Security Monitoring
Course: 1 Hour, 24 Minutes
- Course Overview
- Reviewing Microsoft Defender For Cloud Recommendations
- Monitoring the Performance of Windows Hosts
- Managing Windows Event Viewer Logs
- Enabling Windows Log Forwarding
- Monitoring the Performance of Linux Hosts
- Managing Linux Logs
- Enabling Linux Log Forwarding
- Reviewing Web Server Access Logs
- Monitoring the Performance of Cloud Services
- Threat Positives and Negatives
- Security Information and Event Management (SIEM)
- Security Orchestration, Automation, and Response (SOAR)
- Using Microsoft Sentinel As a SIEM
- Course Summary
| Taal | Engels |
|---|---|
| Kwalificaties van de Instructeur | Gecertificeerd |
| Cursusformaat en Lengte | Lesvideo's met ondertiteling, interactieve elementen en opdrachten en testen |
| Lesduur | 21 uur |
| Voortgangsbewaking | Ja |
| Toegang tot Materiaal | 365 dagen |
| Technische Vereisten | Computer of mobiel apparaat, Stabiele internetverbindingen Webbrowserzoals Chrome, Firefox, Safari of Edge. |
| Support of Ondersteuning | Helpdesk en online kennisbank 24/7 |
| Certificering | Certificaat van deelname in PDF formaat |
| Prijs en Kosten | Cursusprijs zonder extra kosten |
| Annuleringsbeleid en Geld-Terug-Garantie | Wij beoordelen dit per situatie |
| Award Winning E-learning | Ja |
| Tip! | Zorg voor een rustige leeromgeving, tijd en motivatie, audioapparatuur zoals een koptelefoon of luidsprekers voor audio, accountinformatie zoals inloggegevens voor toegang tot het e-learning platform. |
Er zijn nog geen reviews geschreven over dit product.
OEM Office Elearning Menu Top 2 in ICT-trainingen 2024!
OEM Office Elearning Menu is trots op de tweede plaats in de categorie ICT-trainingen 2024 bij Beste Opleider van Nederland (Springest/Archipel). Dank aan al onze cursisten voor hun vertrouwen!
Beoordelingen
Er zijn nog geen reviews geschreven over dit product.